Mcp Server Security Best Practices
Introduction
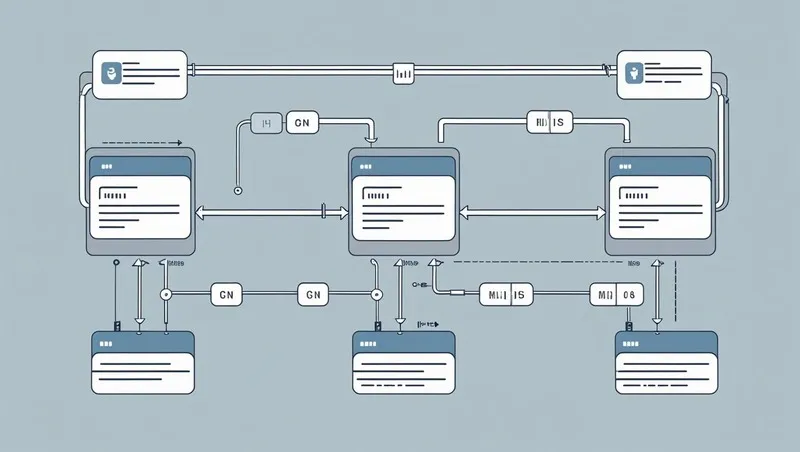
The Model Context Protocol (MCP) is quickly becoming the backbone of how Large Language Models (LLMs) securely connect with enterprise data, tools, and workflows. But with great flexibility comes serious responsibility—an insecure MCP Server can expose sensitive systems and data to breaches, prompt injections, or malicious actors.
In this guide, we’ll walk through MCP Server security best practices, and show how the TrueFoundry MCP Gateway helps enterprises implement these guardrails by default.
Why Securing MCP Servers Is Critical
MCP Servers act as the bridge between AI agents and your enterprise systems—databases, APIs, internal tools. Without proper safeguards:
- Unauthorized users may gain access to sensitive data.
- Agents could misuse tools (e.g., deleting records, escalating privileges).Agents might delete records, escalate privileges, or trigger unsafe actions. Gartner predicts that by 2026, 75% of organizations will adopt AI security tools to prevent misuse【Gartner Emerging Technologies Report, 2023】
- Malicious MCP servers could trick agents into leaking data.A rogue MCP server could trick agents into leaking confidential data. According to MITRE, prompt injection attacks are among the top emerging AI threats【MITRE ATLAS, 2024】
Securing your MCP servers is not optional—it’s the foundation of trustworthy AI adoption.
Core MCP Server Security Best Practices
1. Strong Authentication
- Use OAuth 2.0 / OIDC with enterprise identity providers (Okta, Azure AD, Auth0).
- Avoid static tokens in production—they’re difficult to rotate and audit.
- Enforce short-lived tokens and PKCE for added resilience against interception.
- Where possible, integrate with federated identity for SSO and centralized control.
In the TrueFoundry MCP Gateway, servers can be protected with OAuth 2.0 or Personal Access Tokens, while supporting enterprise IdPs out of the box.
2. Fine-Grained Authorization (RBAC)
- Implement role-based access control: e.g., viewer, user, admin.
- Assign tool-level permissions so only authorized roles can trigger sensitive actions.
- Follow principle of least privilege—never expose more than what’s necessary.
TrueFoundry allows administrators to enforce RBAC directly at the MCP Gateway, ensuring tool access is restricted per user or team.
3. Input Validation & Schema Enforcement
- Validate all incoming JSON-RPC requests against schemas.
- Reject malformed inputs or unrecognized parameters to prevent prompt injection attacks.
- Sanitize data before execution, especially when tools perform database or file operations.
The MCP Gateway supports schema-driven validation, helping enforce safe interactions automatically.
4. Observability & Governance
- Enable structured audit logs—who accessed what, when, and why.
- Monitor latency, errors, and usage patterns to detect anomalies.
- Apply rate limits to prevent abuse or runaway agent loops.
- Track cost usage when LLM calls are tied to billing.
With TrueFoundry, every request is logged and observable with dashboards for compliance and governance.
5. Runtime AI Security
Traditional perimeter controls aren’t enough for AI workloads. MCP Servers must be protected at runtime, where LLMs interact with real data, APIs, and user requests. This is where runtime AI security becomes essential:
- Runtime Threat Detection: Monitor live agent-tool interactions to detect anomalies such as prompt injection, data exfiltration, or malicious tool execution.
- Inline Policy Enforcement: Apply guardrails dynamically—block sensitive data leakage, stop unauthorized write/delete operations, and enforce compliance rules in real-time.
- Data Loss Prevention (DLP): Prevent MCP tools from unintentionally exposing PII, financial data, or confidential IP.
The TrueFoundry MCP Gateway integrates with leading runtime security providers like Palo Alto Prisma and other enterprise security platforms. This means organizations can extend their existing Zero Trust and runtime security policies to MCP servers, without building custom solutions.
With this model, you don’t just configure static policies—you gain continuous runtime protection, aligned with your broader enterprise security stack.
6. Secure Deployment Models
- Run MCP servers in isolated environments (VPCs, namespaces, or containers).
- Avoid exposing servers directly to the public internet unless absolutely required.
- For compliance needs, deploy MCP servers in air-gapped or hybrid environments.
TrueFoundry supports flexible deployment—cloud, on-prem, VPC, or air-gapped—so teams can enforce data sovereignty and compliance easily.
Summary: Checklist for MCP Server Security
Conclusion
MCP Servers are the new API boundaries for AI systems—and securing them is critical to prevent misuse, data leaks, or compliance failures.
By adopting authentication, RBAC, validation, observability, and runtime defenses, you can ensure your MCP servers remain resilient.
With the TrueFoundry MCP Gateway, enterprises get these best practices out-of-the-box, making it easier to deploy MCP securely while accelerating AI adoption.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.