MCP Access Control: Securing AI Agents with an MCP Gateway
Introduction
Enterprise AI has crossed a critical threshold. Running large language models in production is no longer the hard problem. Most organizations already operate multiple models - hosted, self-managed, or hybrid behind standardized inference layers. The real inflection point comes after inference, when models evolve into agents that can discover tools, invoke APIs, and execute real actions across enterprise systems.
This shift is enabled by the Model Context Protocol (MCP). MCP standardizes how models interact with external tools through MCP servers, making agentic workflows modular and interoperable. But MCP is deliberately permissive. It optimizes for flexibility and developer velocity, not for enterprise governance.
Once models can invoke tools, tool access becomes a privileged operation. A single MCP call can read sensitive data, mutate state, or trigger downstream systems. At enterprise scale, this introduces a new security boundary - one that cannot be governed through prompts or application code alone.
This is why MCP access control is no longer optional. It is a prerequisite for running agentic AI safely in production.
Why MCP Access Control Is an Enterprise Requirement
MCP fundamentally changes the trust model of AI systems.
In traditional AI deployments, applications controlled execution and models generated outputs. With MCP, models participate directly in execution paths by selecting and invoking tools at runtime. This creates emergent behavior that is difficult to predict and impossible to secure with static checks.
Without MCP access control, enterprises face concrete risks:
- Over-privileged agents invoking internal or administrative tools
- Cross-environment access, where staging or experimental agents touch production systems
- Compliance violations, especially in regulated or multi-region deployments
- Lack of auditability, with no clear record of which model invoked which tool and why
Critically, these risks cannot be mitigated reliably at the prompt layer or inside MCP servers. Prompts are non-deterministic, and tool-side checks lack global context about the model, agent identity, or environment.
What enterprises need is a central enforcement point that treats MCP tool invocation as a governed action - evaluated against identity, policy, and environment before execution. This is the role of an MCP Gateway, as implemented in platforms like TrueFoundry.
Without this control plane, MCP-based systems remain suitable for experimentation, but not for production.
Why MCP Access Control Must Live in an MCP Gateway
MCP access control fails when it is implemented in the wrong layer. In practice, teams try to secure MCP by:
- Restricting tools via prompt instructions
- Embedding authorization logic inside MCP servers
- Adding checks in agent orchestration code
All three approaches break down in real enterprise environments.
Prompt-based controls are non-deterministic and model-dependent. Agent code is fragmented across teams and repos. MCP servers operate in isolation, with no visibility into which model, which agent, or which environment initiated a request.
MCP access control requires global context:
- Agent or application identity
- Model identity (and trust level)
- Environment (dev, staging, prod)
- Organizational and compliance policy
Only an MCP Gateway can consistently evaluate this context before a tool is invoked.
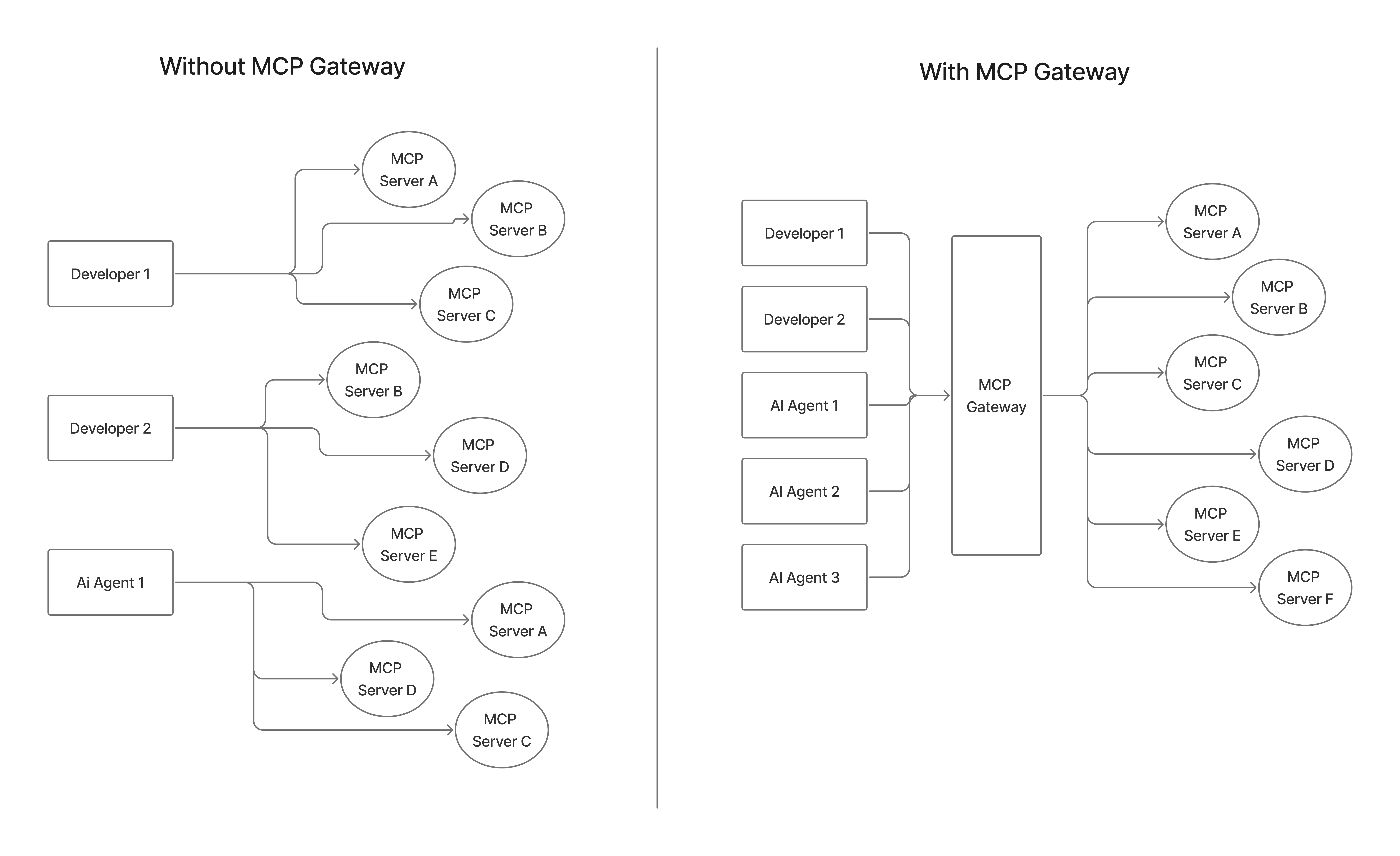
An MCP Gateway sits between models and MCP servers, acting as a policy enforcement point. Every tool discovery and invocation request is intercepted, evaluated, and either allowed or blocked deterministically. This centralization is what enables least-privilege access, consistent governance, and auditability across all agent workloads.
Platforms like TrueFoundry treat the MCP Gateway as a first-class control plane, separate from inference routing and separate from application logic because tool execution represents a distinct trust boundary.
Enterprise Failure Modes Without an MCP Gateway
The absence of an MCP Gateway does not result in theoretical risk - it leads to predictable, repeatable failures at scale.
1. Tool Overexposure
Without centralized control, MCP servers often expose all tools to all agents. This leads to over-privileged agents invoking internal, administrative, or state-mutating tools unintentionally.
2. Cross-Environment Leakage
Experimental agents running in development environments end up invoking production MCP servers, because no global environment-level enforcement exists.
3. Model-Based Privilege Escalation
New or unvetted models are introduced and immediately gain access to sensitive tools, simply because they speak MCP without any model-aware authorization.
4. Audit and Compliance Blind Spots
Security teams cannot answer basic questions:
- Which model invoked this tool?
- Which agent accessed this MCP server?
- Was this invocation policy-compliant?
Without an MCP Gateway, these questions require stitching together logs from multiple systems, often unsuccessfully.
5. Security Logic Sprawl
Each team reimplements access checks differently, leading to inconsistent enforcement and fragile systems that are impossible to reason about holistically.
These failure modes are not edge cases. They are the default outcome when MCP is deployed without a centralized control plane.
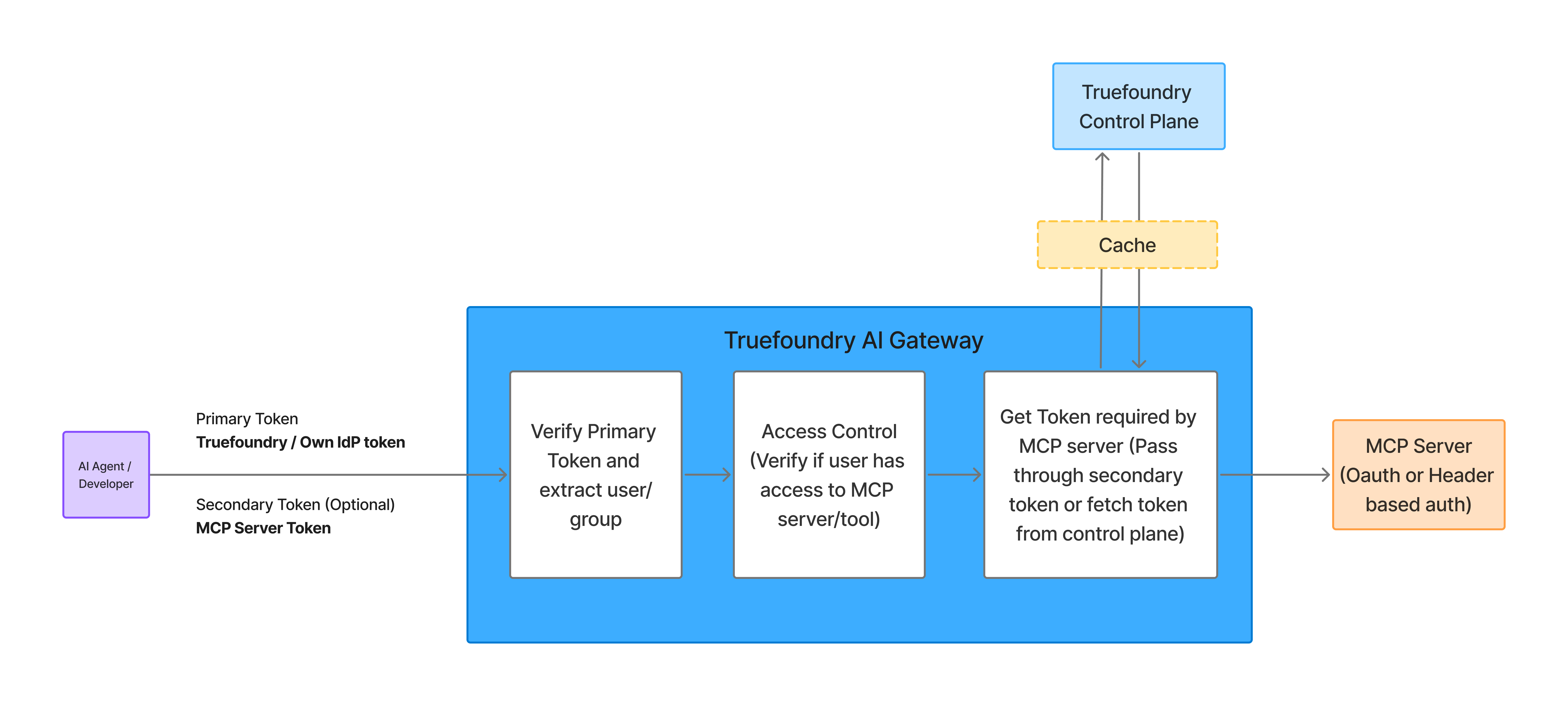
How MCP Access Control Works in TrueFoundry
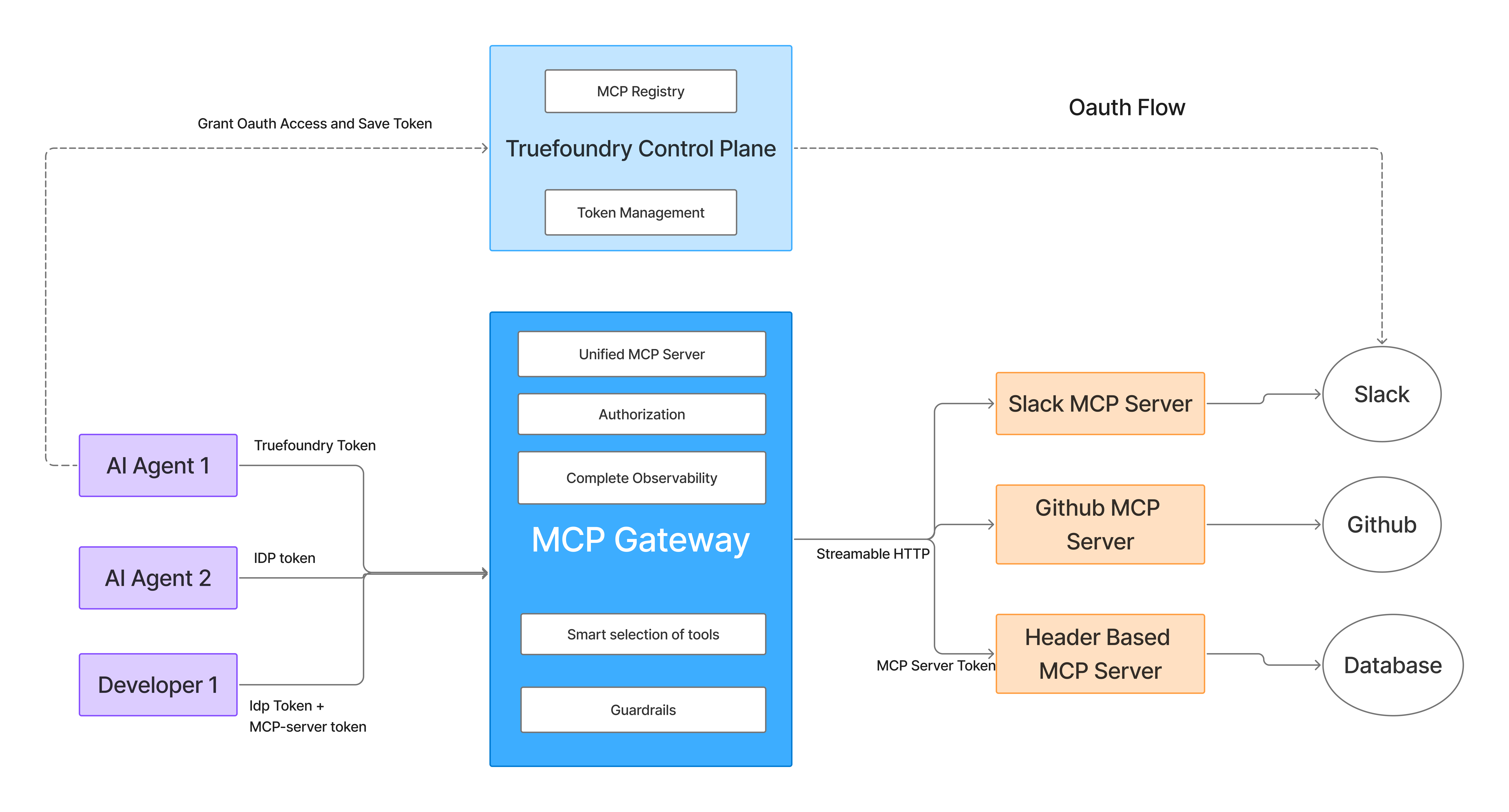
In TrueFoundry, MCP access control is implemented as a first-class capability of the MCP Gateway, not as configuration scattered across agents, prompts, or MCP servers.
The core design principle is simple:
Every MCP interaction is treated as a privileged, policy-evaluated operation.
This applies equally to:
- MCP server discovery
- Tool metadata exposure
- Tool invocation and execution
Nothing bypasses the gateway.
Centralized Policy Evaluation at the MCP Gateway
When an agent running on TrueFoundry attempts to discover or invoke an MCP tool, the request flows through the TrueFoundry MCP Gateway, where it is evaluated across multiple policy dimensions simultaneously:
- Application / agent identity
- Model identity (including model source and trust tier)
- MCP server identity
- Specific tool being accessed
- Environment and workspace context
This context is already known to TrueFoundry because:
- Agents run as managed applications
- Models are provisioned and routed via the platform
- Environments and workspaces are explicit platform primitives
As a result, access decisions are:
- Deterministic (not model-dependent)
- Consistent across agents
- Centralized and auditable
This is fundamentally different from MCP setups where authorization logic lives inside tools or agent code.
TrueFoundry MCP Request Enforcement Flow
- An agent issues a request that requires MCP tool access
- The model attempts tool discovery or invocation
- The request is intercepted by the TrueFoundry MCP Gateway
- The gateway evaluates platform-level access policies
- The request is either:
- Allowed → forwarded to the MCP server
- Denied → blocked before any tool execution
- The decision, inputs, and metadata are recorded for observability
Because enforcement happens before the MCP server is reached, unauthorized tool execution is impossible by design.
This makes MCP access control in TrueFoundry fail-closed, not best-effort.
Tool-Level and Model-Aware MCP Access Control in TrueFoundry
TrueFoundry does not assume that:
- All tools are equal
- All models are equally trusted
- All agents should have identical capabilities
MCP access control is therefore fine-grained by default.
Tool-Level Authorization
Within TrueFoundry, MCP access control operates at the individual tool level, not just at the MCP server boundary.
This enables patterns such as:
- Exposing read-only tools broadly
- Restricting state-mutating tools to specific agents
- Completely hiding sensitive tools from certain workloads
Crucially, unauthorized tools are not visible during tool discovery.
If a model cannot see a tool, it cannot attempt to invoke it.
This prevents accidental or emergent misuse, even in complex agent chains.
Model-Aware Access Control
TrueFoundry treats models as security principals, not interchangeable compute resources.
This enables policies such as:
- Only approved production models can invoke write-capable tools
- Experimental or newly onboarded models restricted to sandbox MCP servers
- External hosted models blocked from accessing internal MCP entirely
Because model routing and MCP access both pass through the platform, these rules are enforced consistently, without requiring agent-level logic.This eliminates an entire class of failures where a new model gains unintended access simply because it supports MCP.
In TrueFoundry, MCP access control is not layered on top of agent execution - it is embedded into the platform’s control plane.
That means:
- No duplicated security logic across teams
- No reliance on prompt discipline
- No hidden trust assumptions
MCP becomes safe to use at scale because tool invocation is governed as rigorously as model inference.
Environment & Data Residency Enforcement for MCP in TrueFoundry
In enterprise deployments, MCP access control is inseparable from environment and data residency guarantees.
Agentic AI systems rarely operate in a single, flat environment. In practice, organizations run:
- Multiple workspaces or tenants
- Distinct environments (dev, staging, prod)
- Region-specific deployments to meet regulatory requirements
Without explicit enforcement, MCP introduces a high-risk failure mode:
tools deployed in one environment or region being invoked by agents from another.
How TrueFoundry Enforces Environment Isolation
In TrueFoundry, environment context is a first-class primitive. Every agent, model, and MCP server is explicitly associated with:
- A workspace
- An environment
- A region (where applicable)
The MCP Gateway enforces this context at runtime.
This enables policies such as:
- Production agents can only invoke production MCP servers
- Development or experimental agents are sandboxed
- Cross-environment MCP calls are blocked by default
Because enforcement happens at the gateway, these guarantees hold even if agent code is misconfigured.
Data Residency–Aware MCP Access Control
For regulated industries, MCP access control must also respect data locality constraints.
TrueFoundry enables:
- Region-scoped MCP servers
- Region-aware policy evaluation
- Blocking of cross-region MCP tool invocation
This ensures that:
- Data accessed via MCP never leaves its allowed geography
- Models running in one region cannot invoke tools in another
- Compliance requirements (GDPR, financial regulations, internal policies) are enforced by design
Critically, this is not a documentation promise. It is a runtime guarantee enforced by the MCP Gateway.
Observability, Tracing, and Auditability for MCP Access Control
Access control without observability is incomplete.
In production environments, security and platform teams must be able to answer questions like:
- Which agent invoked this tool?
- Which model initiated the request?
- Was the invocation policy-compliant?
- What data or system was accessed?
TrueFoundry treats MCP access events as first-class observable signals.
End-to-End MCP Tracing
Every MCP interaction passing through the TrueFoundry MCP Gateway is traced, including:
- Tool discovery requests
- Tool invocation attempts
- Policy allow / deny decisions
- Execution metadata
These traces are linked to model inference traces, providing a unified view of:
User request → model reasoning → tool invocation → outcome
This makes it possible to debug agent behavior, investigate incidents, and understand emergent workflows without guesswork.
Audit-Ready Access Logs
TrueFoundry generates structured logs for MCP access decisions, capturing:
- Agent or application identity
- Model identity
- MCP server and tool name
- Environment and region
- Policy decision and reason
This enables:
- Security audits
- Compliance reporting
- Post-incident forensics
Most importantly, it allows organizations to prove that MCP access policies are enforced - not just intended.
MCP Access Control vs Prompt-Based Guardrails
As agentic AI systems grow more autonomous, many teams attempt to “secure” tool usage through prompt-based instructions or agent-side conventions. In early experiments, this may appear to work. At enterprise scale, it fails predictably.
Prompt-based guardrails are:
- Non-deterministic — models may ignore or reinterpret instructions
- Model-dependent — behavior changes across model versions
- Unauditable — no authoritative record of enforcement
- Easy to bypass — intentionally or accidentally
Most importantly, prompts operate inside the model. MCP access control must operate outside the model.
In TrueFoundry, MCP access control is enforced by the MCP Gateway, before any MCP server or tool is reached. This makes enforcement:
- Deterministic
- Model-agnostic
- Centralized
- Auditable
Conclusion
The Model Context Protocol makes agentic AI systems practical at scale but it also introduces a new execution boundary that traditional AI security models were never designed to handle. Once models can discover and invoke tools dynamically, tool access becomes a privileged operation that must be governed with the same rigor as APIs, infrastructure, and data.
MCP access control cannot be reliably enforced through prompts, agent code, or tool-side checks. Those approaches fragment policy, lack global context, and fail under multi-model, multi-environment deployments. What enterprises need instead is a dedicated MCP Gateway that enforces access centrally, deterministically, and audibly, before any tool is executed.
In practice, MCP access control is not an optional feature or a future enhancement. It is the control boundary that determines whether agentic AI remains an experimental capability or becomes a production-grade system enterprises can confidently depend on.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.