How to Detect Shadow AI and Turn Risk into Enterprise Advantage
It’s 4:30 PM on a Thursday. Alex, a senior backend engineer at your company, is staring down a deadline and a particularly nasty regular expression bug that is blocking the weekly release.
The "official" path involves opening a Jira ticket to request access to the corporate-approved AI coding assistant, waiting for IT approval, waiting for procurement provisioning, and missing the release window.
The "unofficial" path takes thirty seconds. Alex installs a free browser extension called "CodeWizard-GPT," copy-pastes the proprietary code snippet into the sidebar, and gets the fix instantly. The code ships. The day is saved.
But what happened to that code snippet? Did it contain hardcoded environment variables? Did the browser extension require permissions to read all data on internal dashboards?
This is the "Alex Paradox." Your workforce is using AI to achieve unprecedented levels of productivity, often with the best intentions. Yet, this decentralized adoption—Shadow AI—creates an invisible architecture of unvetted vendors, data leakage risks, and unpredictable costs.
At TrueFoundry, we believe that Shadow AI isn't a disciplinary issue; it's an infrastructure signal. It means your team needs a paved path to innovation.
Here is how to detect the current state of Shadow AI in your enterprise and how to transition from chaotic adoption to governed acceleration using the TrueFoundry Platform.
The Anatomy of Shadow AI Traffic
Unlike traditional shadow IT, which was often about bypassing procurement for cheaper software, Shadow AI is about bypassing friction for faster intelligence. It rarely looks like malicious activity. It looks like work is getting done.
Below is a visualization of the current, often chaotic state of enterprise AI consumption:

As the diagram illustrates, data is leaving the secure perimeter through various unmonitored channels. To bring this activity into the light, we must look for specific signals across financial, identity, and network layers.
Practical Detection Methods
Detecting Shadow AI requires triangulating data from different parts of the IT stack. We have compiled the most effective signals into the table below:
The Diplomatic Path Forward: Don't Block, Pave.
Upon discovering the extent of Shadow AI, the institutional reflex is often to block domains and ban extensions. While understandable from a compliance perspective, this approach is often counterproductive.
Blocking tools without providing viable alternatives does not eliminate the risk; it merely drives it further underground—to personal devices and cellular hotspots—where visibility is reduced to zero. Furthermore, it signals to your engineering talent that security is an impediment to velocity, rather than an enabler.
The TrueFoundry Paradigm: Centralized Governance, Decentralized Innovation
The goal is not to stop "Alex" from fixing the bug quickly. The goal is to ensure Alex fixes the bug quickly using infrastructure that is secure, cost-controlled, and compliant by default.
TrueFoundry allows enterprises to wrap governance around AI adoption without sacrificing the developer experience. By shifting from direct vendor access to a centralized AI Gateway, you gain immediate control.
1. Instant Visibility and Cost Attribution
Instead of hunting through expense reports, the TrueFoundry AI Gateway provides a single pane of glass for all AI spending. You can attribute costs to specific teams, projects, or even individual developers in real-time, allowing for accurate chargebacks and budget alerts.
2. Guardrails as a Safety Net
You no longer need to trust that developers won't paste PII into a prompt. TrueFoundry Guardrails intervene before data leaves your perimeter. You can configure policies to automatically redact sensitive information (like SSNs, credit cards, or secrets) or block prompts that violate corporate policy—all without slowing down the developer.
The Next Frontier: Securing "Agentic" Shadow AI with MCP
While most enterprises are still grappling with Chatbots, your most advanced engineers (like Alex) are already moving to the next level: AI Agents.
Alex isn't just chatting with GPT-4 anymore. Alex is building an agent that can read Jira tickets, search Confluence docs, and query the production database to solve problems automatically.
To do this, Alex needs to give the AI access to these tools. In a "Shadow" environment, this leads to Credential Sprawl: Alex hardcodes a Jira Personal Access Token (PAT) and a Database Connection String directly into the Python script. If that script leaks, your internal systems are compromised.
This is where TrueFoundry’s support for the Model Context Protocol (MCP) becomes your security superpower.
How TrueFoundry MCP Auth Solves the "Keys to the Kingdom" Problem
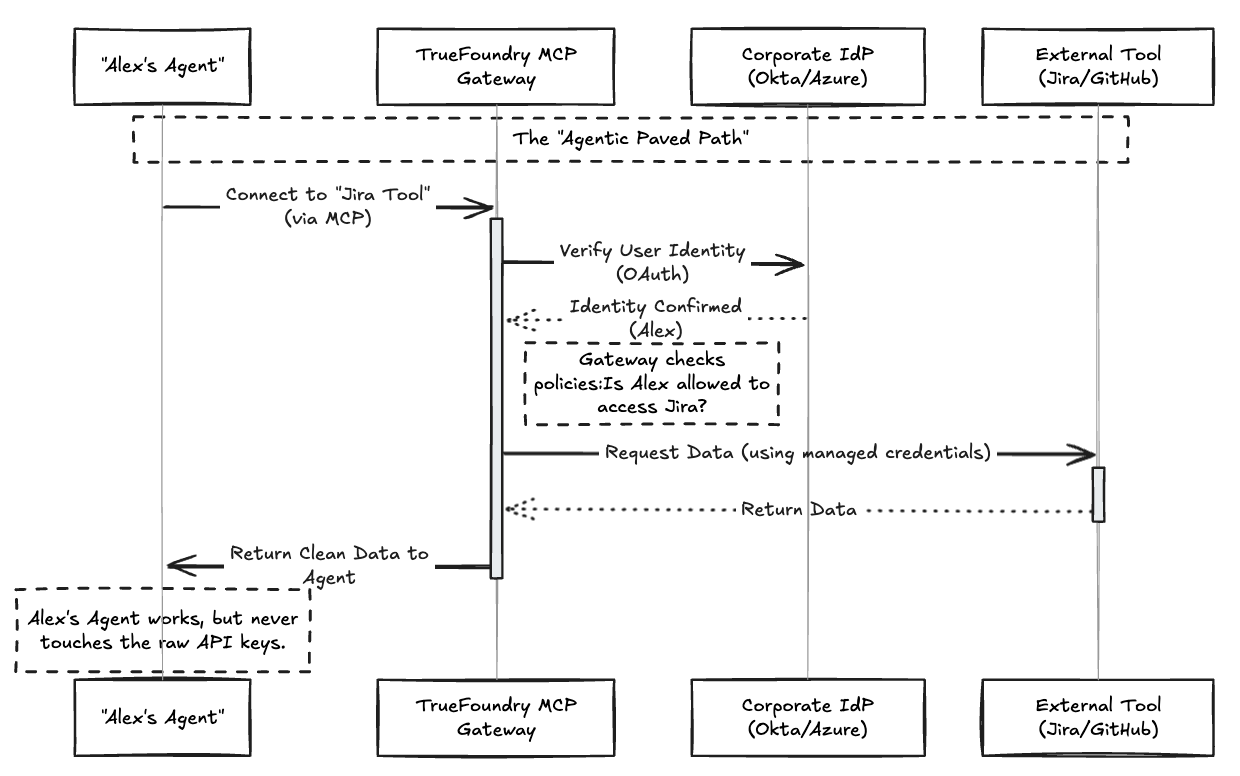
TrueFoundry acts as a secure broker between your AI agents and your internal tools using the Model Context Protocol (MCP). Instead of hardcoding keys, the agent authenticates with TrueFoundry, and TrueFoundry handles the handshake with the downstream tools (GitHub, Slack, Jira, etc.).
The Secure Workflow: Visualized
By routing agentic traffic through the TrueFoundry MCP Gateway, you transform a security liability into a managed capability.
Why This Matters for 2026
We are entering the era of "Agentic Sprawl." Just as you had to manage SaaS sprawl in 2020, you must manage Agent sprawl today. TrueFoundry’s MCP Architecture ensures that identity is the new perimeter. It allows your developers to build powerful, autonomous agents without ever exposing the "keys to the kingdom."
Conclusion: Visibility is Security
Shadow AI is not a malicious act; it’s an innovation signal. Your employees want to move faster.
The "Alex Paradox" is only a paradox if you force a choice between security and speed. By using TrueFoundry, you don't have to choose. You can detect the usage, migrate it to a centralized Gateway, and secure the future of Agentic AI with robust MCP authentication.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.







.png)
.png)








