Top 5 Obot MCP Gateway Alternatives
The Model Context Protocol (MCP), introduced by Anthropic in late 2024, quietly rewired how we connect AI agents to the tools and data they need. Instead of brittle, one-off integrations, MCP standardizes the “adapter” layer so agents can talk to services like Slack, Jira, or GitHub with far less custom work. That’s powerful — and messy. As companies deploy LLM-powered agents, they’re spinning up thousands of MCP servers. Without a control plane, that growth quickly becomes integration chaos: duplicate connectors, scattered credentials, and little visibility into who’s giving AI access to what.
Obot MCP Gateway (launched by Obot AI in August 2025) attempts to solve this. Think of it as both an internal App Store and an air-traffic controller: a central control plane where IT can onboard, secure, and monitor MCP servers while employees discover and connect approved tools.
While Obot offers a well-designed open-source approach, enterprises often need deeper observability, multi-cloud support, and governance — capabilities where TrueFoundry MCP Gateway and other advanced alternatives lead.
This guide explores how Obot works, where it fits, and five top alternatives to Obot MCP Gateway for enterprise-scale AI infrastructure.
What is Obot MCP Gateway?
Obot is an open-source control plane for MCP servers designed for enterprise governance. At its core it solves three everyday problems: discovery (how employees find the tools they’re allowed to use), access control (who’s allowed to call which MCP), and observability (who did what, when, and how often). The result is fewer “shadow” MCPs running unchecked and more consistent, auditable connections between agents and enterprise systems.
Practically, Obot bundles a service registry, a web-based catalog, RBAC and policy enforcement, credential management, and proxying. Admins can add MCP entries via a UI or GitOps, attach docs and metadata, and publish a curated catalog to employees. Users then pick a tool and get a one-time connection URL that plugs into an LLM client — no manual auth or hand-wiring required. Meanwhile, Obot enforces the policies and sits between the client and the MCP server to provide centralized logging and auditing.
Put simply: Obot gives IT teams the tooling to treat MCP servers like first-class, governed infra instead of a fast-growing set of ad-hoc connectors.
How does Obot MCP Gateway work?
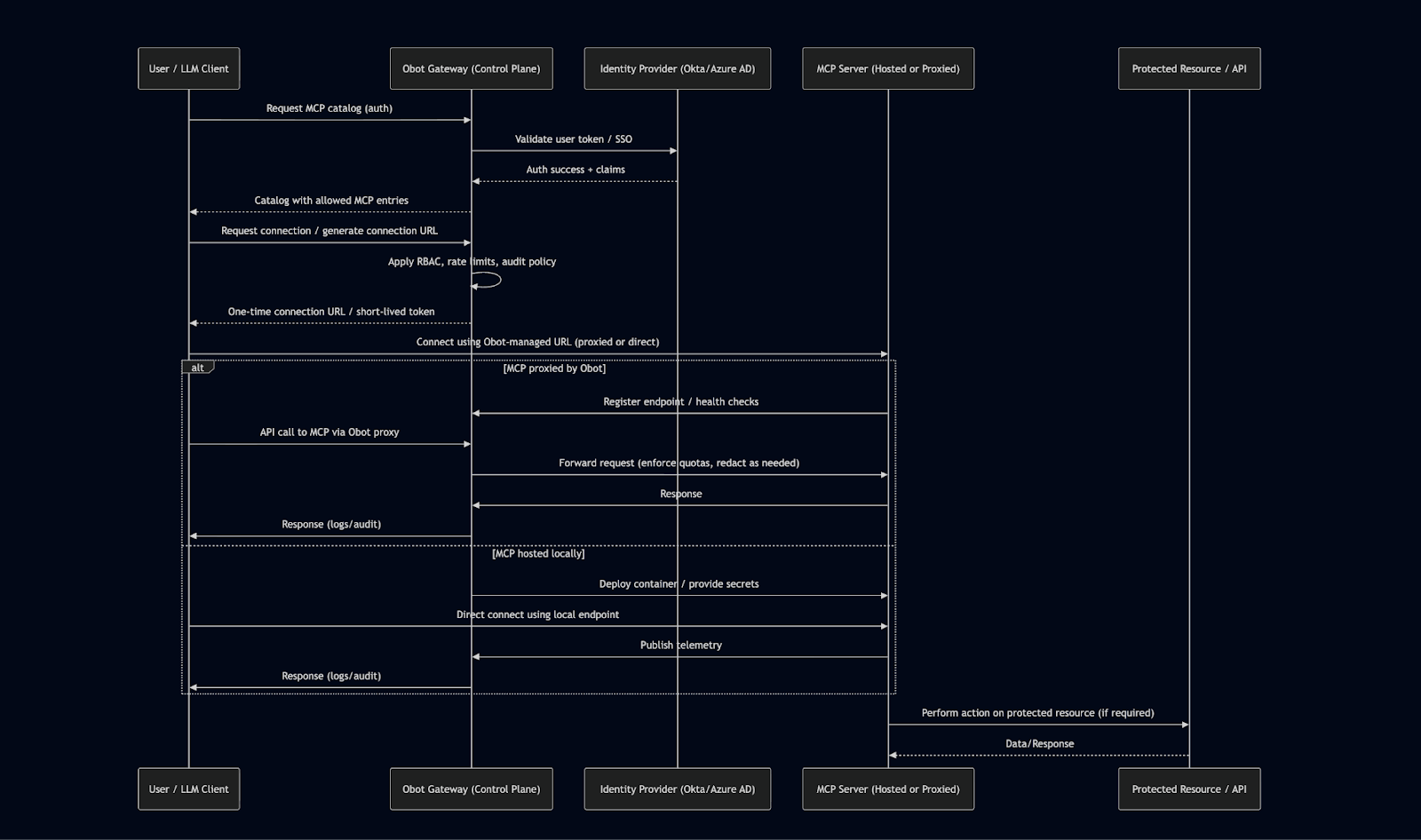
Under the hood, Obot functions as a secure proxy and control plane for all MCP traffic. The typical workflow is as follows:
Admin Setup & Integration
IT deploys the Obot Gateway (often on Kubernetes) and integrates it with identity providers like Okta, Azure AD, or Google Workspace for unified authentication.
Catalog Configuration
Obot includes common MCP connectors (Slack, GitHub, Notion, etc.) out of the box. Admins can add more through a UI or GitOps workflow, tagging each with metadata and usage docs.
Access Control & Policies
Administrators define which teams can access which MCP servers. Policies are enforced directly by Obot’s gateway.
User Discovery & Connection
Employees browse a web catalog of approved MCPs, connect via one-click URLs, and instantly authorize their AI tools to use the selected service.
Routing & Observability
Every MCP request passes through Obot’s proxy layer, providing a unified audit trail, request logs, and performance metrics for compliance and debugging.
Why explore Obot MCP Gateway Alternatives?
While Obot MCP Gateway offers a strong open-source foundation for managing Model Context Protocol servers, it’s primarily designed for lightweight, internal use cases.
Enterprises operating at scale — with hundreds of agents, strict compliance needs, and multi-cloud deployments require deeper governance, observability, and performance optimization.
Key considerations include:
Security & Compliance: Some gateways (like Lasso Security) focus on advanced security controls and real-time scanning of agent calls. An enterprise handling sensitive or regulated data may prefer a gateway with built-in guardrails and threat detection.
Integration Ecosystem: Obot provides many connectors, but other vendors (e.g. TrueFoundry, Microsoft Azure Gateway) offer deeper integration with specific platforms or services. For example, if an organization is heavily invested in Azure, Microsoft’s MCP gateway (which is built into Azure services) might fit more smoothly into existing workflows.
Performance & Scalability: Gateways differ in their overhead and throughput. TrueFoundry’s MCP gateway, for instance, touts sub-3ms latency under load by handling auth and rate limits in-memory. If thousands of concurrent tool calls are expected, performance-optimized solutions may be preferred.
Deployment Model: Some teams prioritize container-native approaches. Docker’s MCP Gateway treats each MCP as a sandboxed container with strict resource limits and security boundaries. Enterprises already using Docker may find that approach familiar and easy to adopt.
Flexibility & Extensibility: Alternatives may offer plugin architectures or unique features. Lasso’s open-source gateway, for instance, lets users add custom security interceptors to filter or transform requests. Other platforms (like IBM’s Context Forge) allow composing “virtual” MCP servers from existing APIs.
Top 5 Obot MCP Gateway Alternatives
1. Truefoundry
TrueFoundry MCP Gateway is an enterprise-grade solution designed to unify and govern large-scale MCP deployments. Built as part of the TrueFoundry AI Platform, it provides a single control plane that seamlessly integrates with existing AI infrastructure — including LLM management, telemetry, and compliance enforcement — enabling teams to manage both models and tools without fragmentation.
Key Features
- Unified Registry (“MCP Server Groups”) — logically isolates and manages toolsets across teams and environments.
- Ultra-Low Latency — benchmarked at sub-3 ms per request, enabled by in-memory routing and optimized concurrency.
- Enterprise-Grade Security — includes federated login (Okta, Azure AD), fine-grained RBAC, and OAuth2 token management.
- Comprehensive Observability — full structured tracing, token analytics, and end-to-end telemetry for every agent call and model query.
- Automated MCP Management — supports containerized MCP deployment, load balancing, and failover orchestration.
- Tight Ecosystem Integration — unified billing, usage tracking, and observability across all models and MCP tools.
Because it’s deeply integrated into the TrueFoundry ecosystem, enterprises gain a single-pane-of-glass view of all AI activity — from LLMs to connected tools — ensuring consistent governance, compliance, and performance visibility.
In short, TrueFoundry MCP Gateway is more than just a connector — it’s a complete AI infrastructure control plane. For organizations that need scale, reliability, and compliance, TrueFoundry stands out as the most comprehensive alternative to Obot.
For enterprises evaluating the best MCP gateway for scale, compliance, and performance, TrueFoundry offers a unified control plane purpose-built for production-grade AI systems.
Obot vs. TrueFoundry MCP Gateway: Feature Comparison
Why TrueFoundry Stands Out
TrueFoundry goes beyond being a gateway — it’s a complete orchestration and governance platform for AI infrastructure.
By unifying model management, observability, and policy enforcement under one system, TrueFoundry eliminates integration sprawl and provides a single pane of glass for all AI agent activity.
Its sub-3 ms latency, deep observability, and enterprise-grade compliance make it the preferred choice for organizations building scalable, secure, and compliant AI systems.
2. Docker MCP Gateway
Docker MCP Gateway is a container-native solution offered as a Docker plugin, aimed at teams already familiar with containerization workflows. It treats each MCP server as a containerized workload with strong isolation and resource caps, aggregating multiple MCP servers behind a single, secure interface. A standout feature is its Interceptor Framework — allowing custom scripts or plugins to inspect, modify, or block requests in real time.
For example:
- A “before” interceptor might enforce a one-repo-per-session rule on GitHub calls.
- An “after” interceptor can log responses or mask secrets automatically.
Docker’s MCP Gateway excels at security filtering and auditability, with tight integration into Docker Desktop and Docker Swarm. The trade-off is added latency (50–200 ms typical round trip) and a container-centric model, but for teams already using Docker infrastructure, it offers familiarity and strong isolation by default.
3. IBM MCP Gateway
IBM’s Context Forge is an open-source MCP gateway and registry designed for large enterprises needing federation and extensibility. It can auto-discover multiple gateways via mDNS, merge capabilities from different deployments, and even compose several MCP servers into a single endpoint.
Key highlights:
- Supports multiple authentication schemes (JWT, Basic Auth, custom headers).
- Encrypts tool credentials and integrates with Postgres, MySQL, or SQLite databases.
- Converts REST APIs into MCP servers on the fly for flexible integration.
Context Forge feels like traditional IBM middleware — highly configurable, federation-friendly, and security-conscious.
However, it’s still in beta and lacks official enterprise support, making it best suited for organizations with strong DevOps capabilities that can manage a DIY setup.
4. Microsoft MCP Gateway
Instead of offering a standalone gateway, Microsoft has integrated MCP functionality directly into its Azure ecosystem. The Azure MCP Gateway acts as a session-aware reverse proxy for Kubernetes-hosted MCP servers and connects with Azure API Management, Container Apps, and Azure Monitor.
- Native Azure AD integration handles authentication and policy enforcement.
- OAuth flows, rate limits, and logging are managed through existing Azure services.
- Ideal for Azure-centric teams seeking low setup overhead and consistent cloud-native governance.
While this offers deep Azure integration and simplified operations, multi-cloud or on-prem setups can be more complex, and customization options are limited.
In essence, Microsoft’s approach favors convenience and ecosystem alignment over portability.
5. Lasso Security MCP Gateway
Lasso Security’s MCP Gateway is an open-source, security-first gateway focused on risk management and threat detection. It acts as a proxy and orchestrator for all MCP interactions, embedding security, governance, and monitoring into every request.
Key differentiators include:
- Agentic threat detection and data-leak prevention at the protocol level.
- Configurable security filters to scrub credentials and block suspicious behavior.
- Real-time threat scoring, token masking, and malicious code inspection via plugins.
- Unified visibility dashboards ensuring no “off-screen” agent activity.
While the deep security layer can introduce some overhead, Lasso is ideal for regulated industries or security-first organizations needing strict auditability and policy control.
Conclusion
The Obot MCP Gateway represents an important step forward in unified AI integration — offering a free, open-source control plane that introduces governance, scalability, and interoperability to modern MCP deployments.
However, as AI agent adoption accelerates across enterprises, the need for robust, production-grade gateways becomes increasingly critical.
Platforms like Obot and TrueFoundry emphasize low-latency orchestration and end-to-end lifecycle management, while vendors such as Docker, IBM, and Microsoft extend their existing infrastructure ecosystems to meet AI workload demands. Meanwhile, security-first gateways like Lasso Security embed threat detection and compliance enforcement directly within the communication layer — safeguarding AI-to-tool interactions at scale.
By carefully comparing these approaches, enterprises can select an MCP gateway that best fits their architecture, governance, and performance objectives.
In the long run, this evolving ecosystem will empower organizations to confidently connect AI agents with real-world systems — ensuring that security, reliability, and flexibility remain central to every deployment.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.