Secrets are synced from your secret
manager to Truefoundry by default every 1 hour - so please make sure that the values remain correct in your secret manager. This allows auto-rotation of
secrets to also work since values are fetched every hour.
Connect Your Secret Store to TrueFoundry
Integrate your secret store with TrueFoundry (e.g. AWS SSM, GCP Secret Manager, HashiCorp Vault, Azure Vault). This is required for both options below.
To connect your Secret store, navigate to 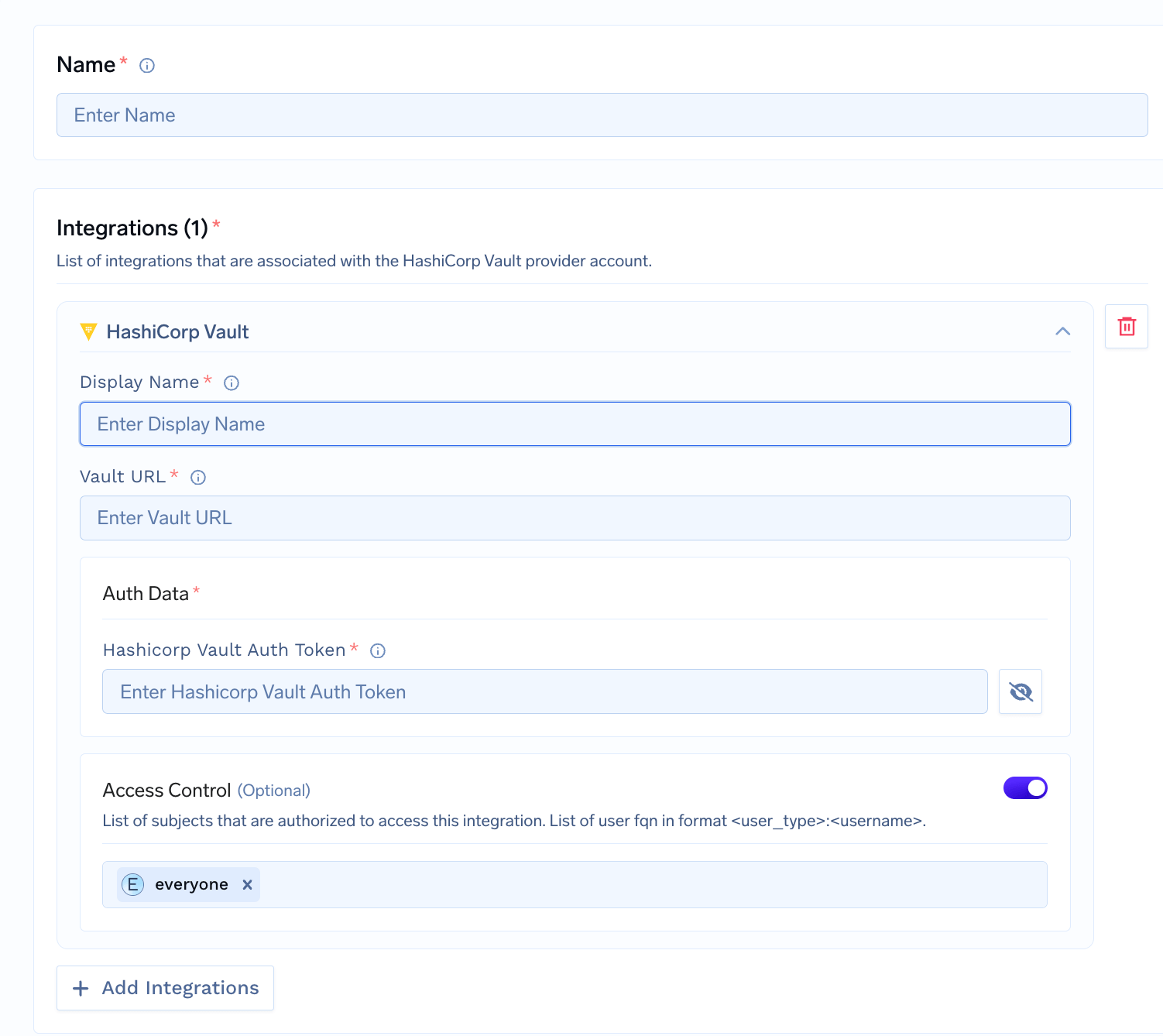
Platform > Integrations and add the Integration for your provider. We support AWS SSM, GCP Secrets manager, Azure Vault and Hashicorp.
TrueFoundry does not store the secret values; they live in your secret
manager. You get a reference to use in deployments and integrations. See
integrate a secret manager for setup.
Use the Secret in an Integration
When adding or editing an integration—such as a Model provider (e.g. OpenAI), MCP server, or Guardrail—use one of the two options below in any API key or sensitive field instead of pasting the raw value.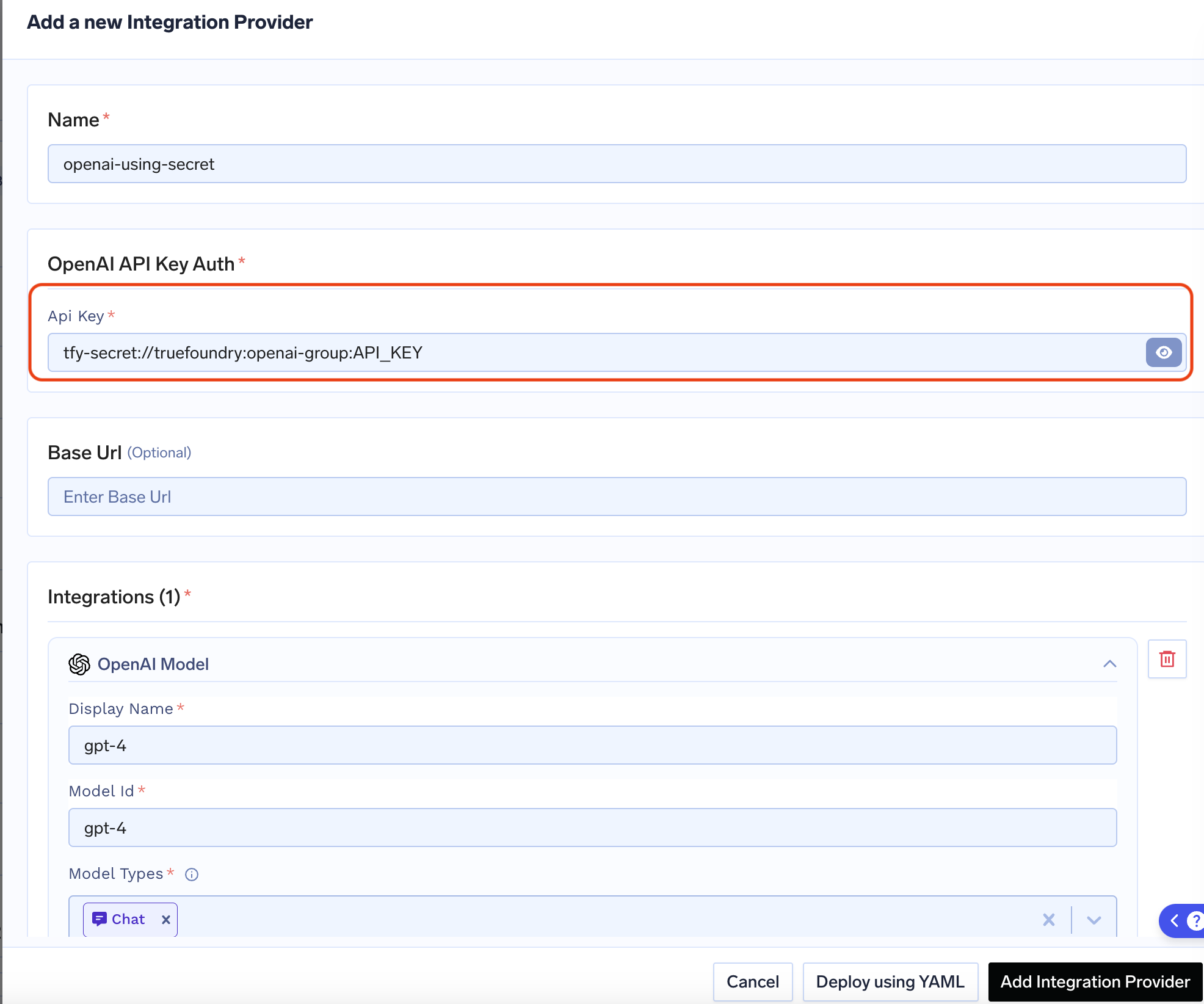

Option A: Create the secret in TrueFoundry, then add the secret FQN
Option A: Create the secret in TrueFoundry, then add the secret FQN
Create the secret in a secret group in TrueFoundry, then use its fully-qualified name (FQN) in the integration.Format: 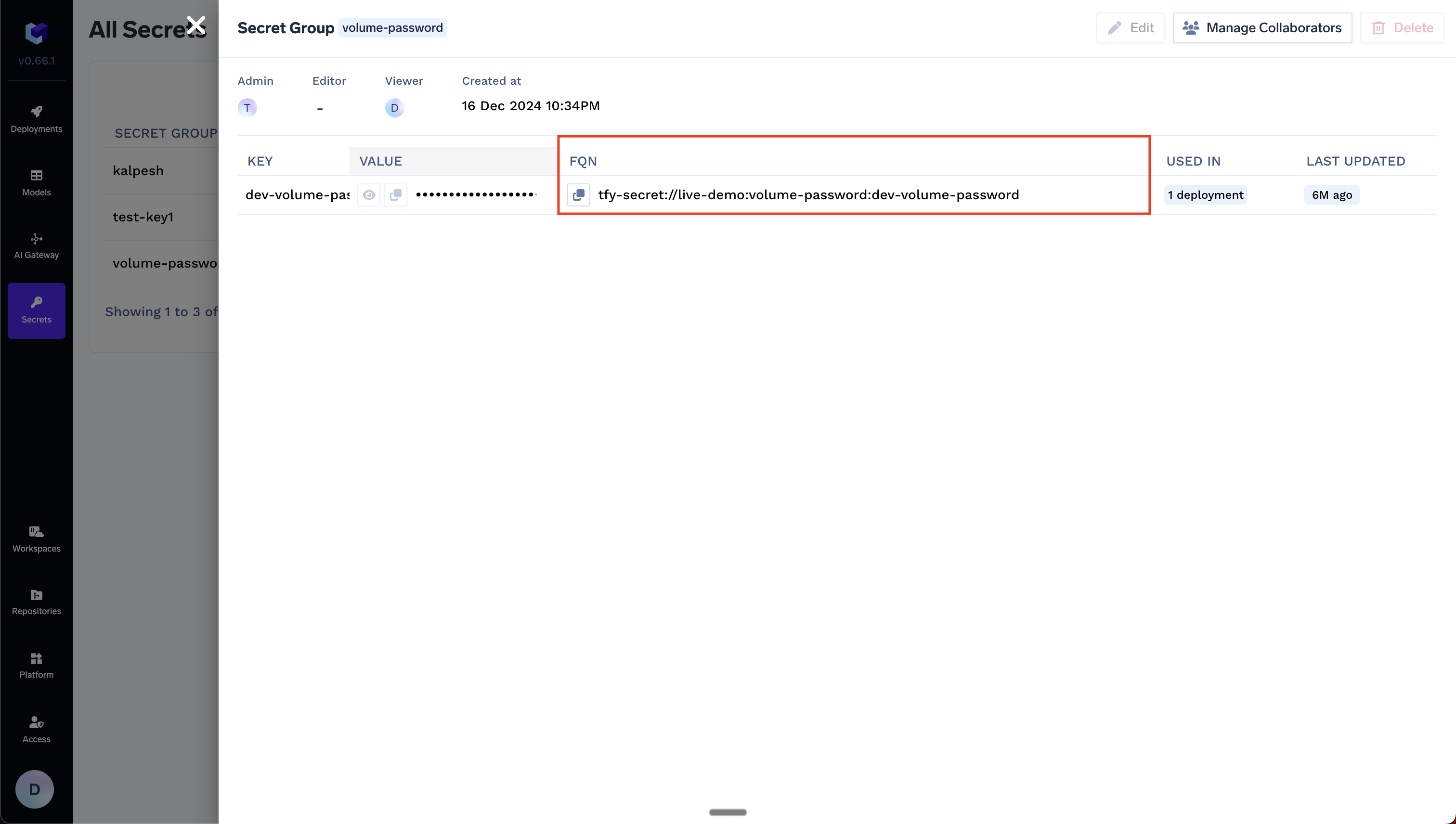
tfy-secret://<tenant>:<secret-group>:<secret-key>Example: For tenant my-tenant, secret group openai-keys, and key OPENAI_API_KEY:
Option B: Use any existing secret in your secret manager directly
Option B: Use any existing secret in your secret manager directly
Use a secret that already exists in your secret manager. You do not create the secret in TrueFoundry—reference it by your secret store FQN and the path in your store.Format: You can find the Secret Store FQN on Platform → Integrations, as shown below: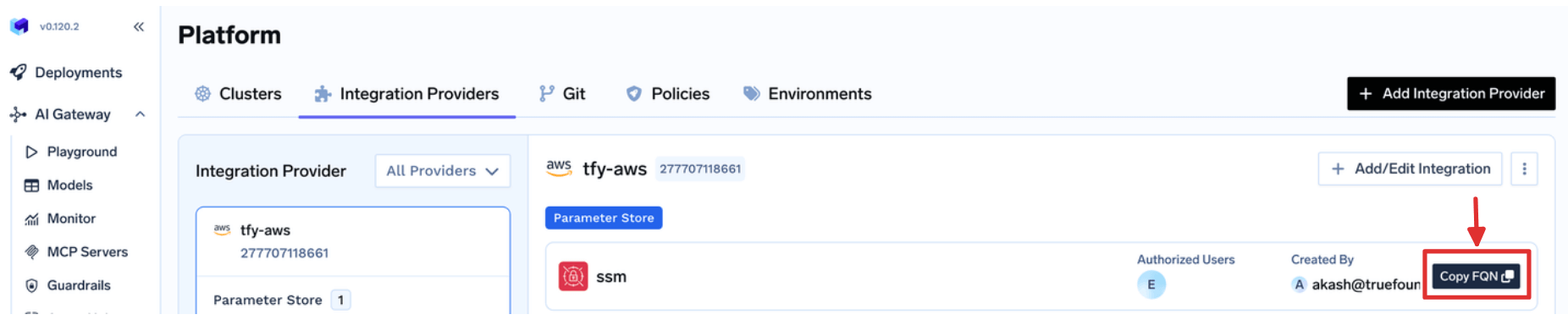
<secret-store-fqn>::<path-to-secret-in-secret-manager>Example: If your secret store FQN is my-tenant:aws:my-aws-provider:secret-store:aws-ssm and the secret path is /tfy-secret/openai/api-key: