1
Add an MCP Server
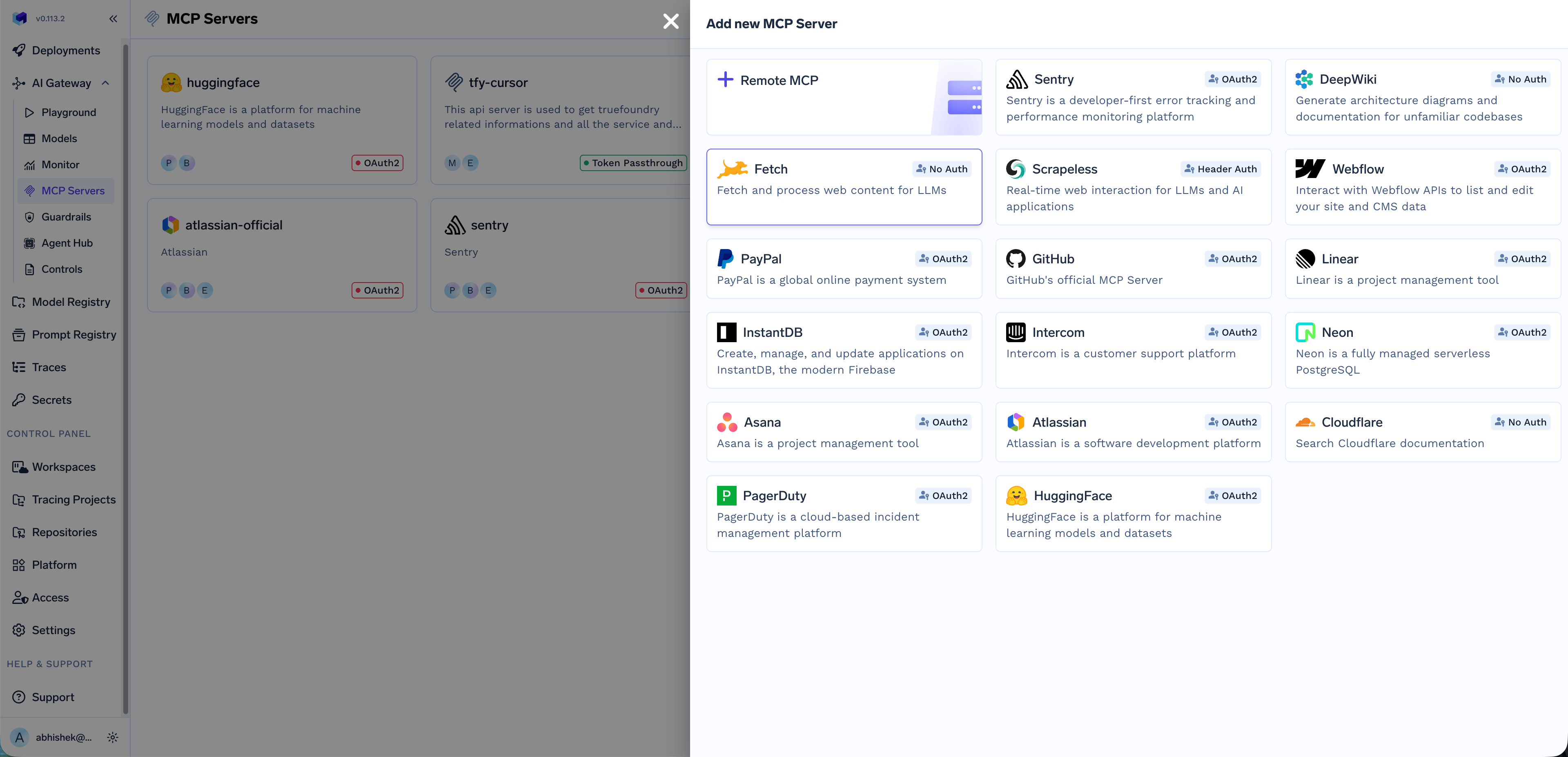
To add an MCP server, you can either create one from scratch or add a public MCP server.
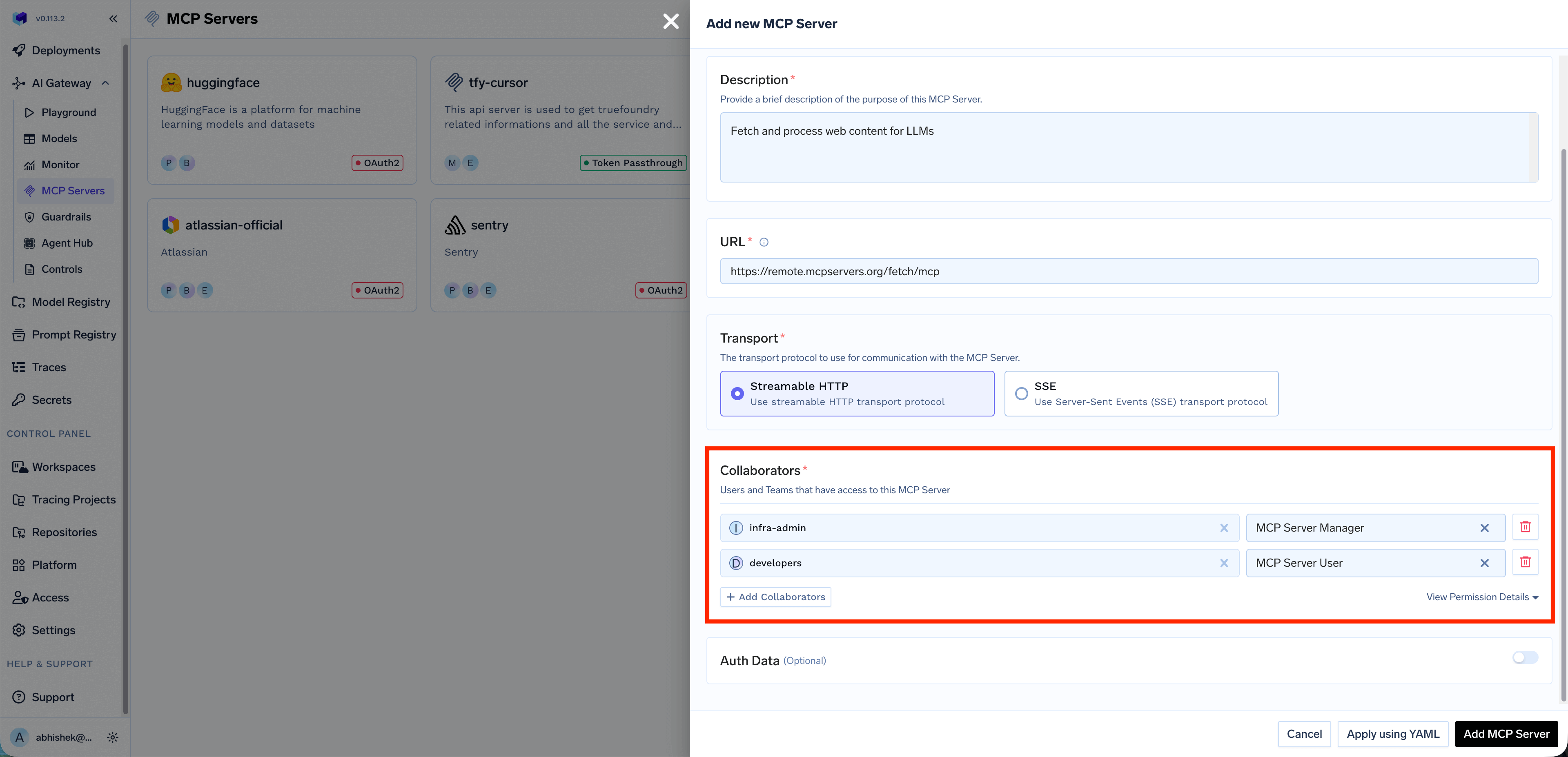
Click + Add Collaborators to add more users or teams. You can also click View Permission Details to see the complete list of permissions for each role.When registering an MCP server, choose the authentication type that determines how requests are authenticated with the upstream MCP server.


Remote MCP button and then provide the following details:| Field | Description |
|---|---|
| Name | A descriptive name for the MCP server |
| Description | A description of the MCP server |
| URL | The URL of the MCP server |
| Transport | streamable-http or sse. Note that sse is deprecated |
Collaborators
The Collaborators section allows you to control who can access and manage this MCP server. You can add individual users or entire teams and assign them specific roles:
| Role | Description |
|---|---|
| MCP Server Manager | Full access to manage the MCP server, including editing configuration, managing collaborators, and deleting the server |
| MCP Server User | Can use the MCP server’s tools in the playground and IDEs, but cannot modify server settings |
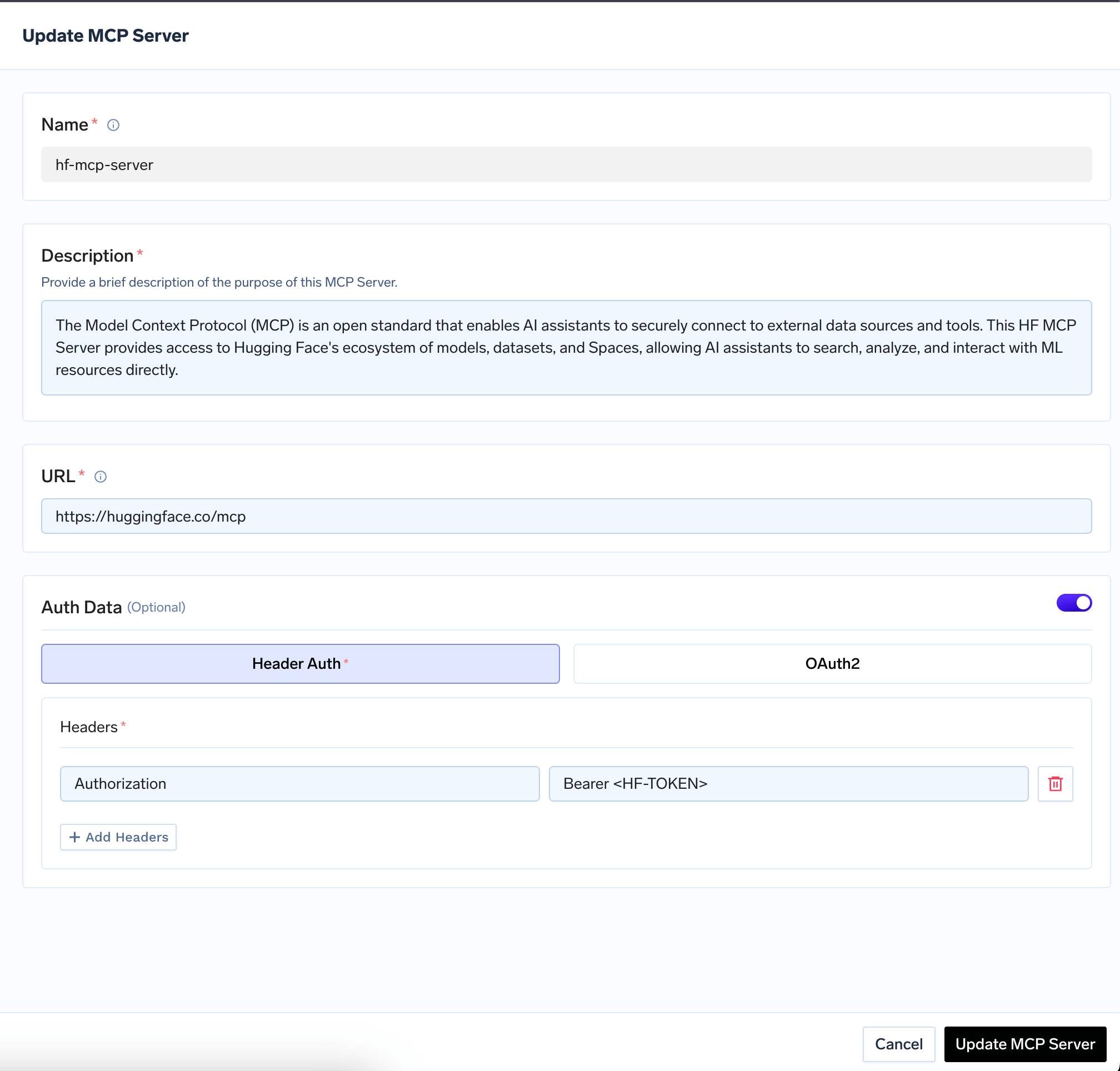
Auth Data
You need to specify the authentication mechanism for the MCP Server:No Auth, Header Auth, DCR, or OAuth2.No Auth
No Auth
The MCP server can be accessed without authentication. This is suitable for: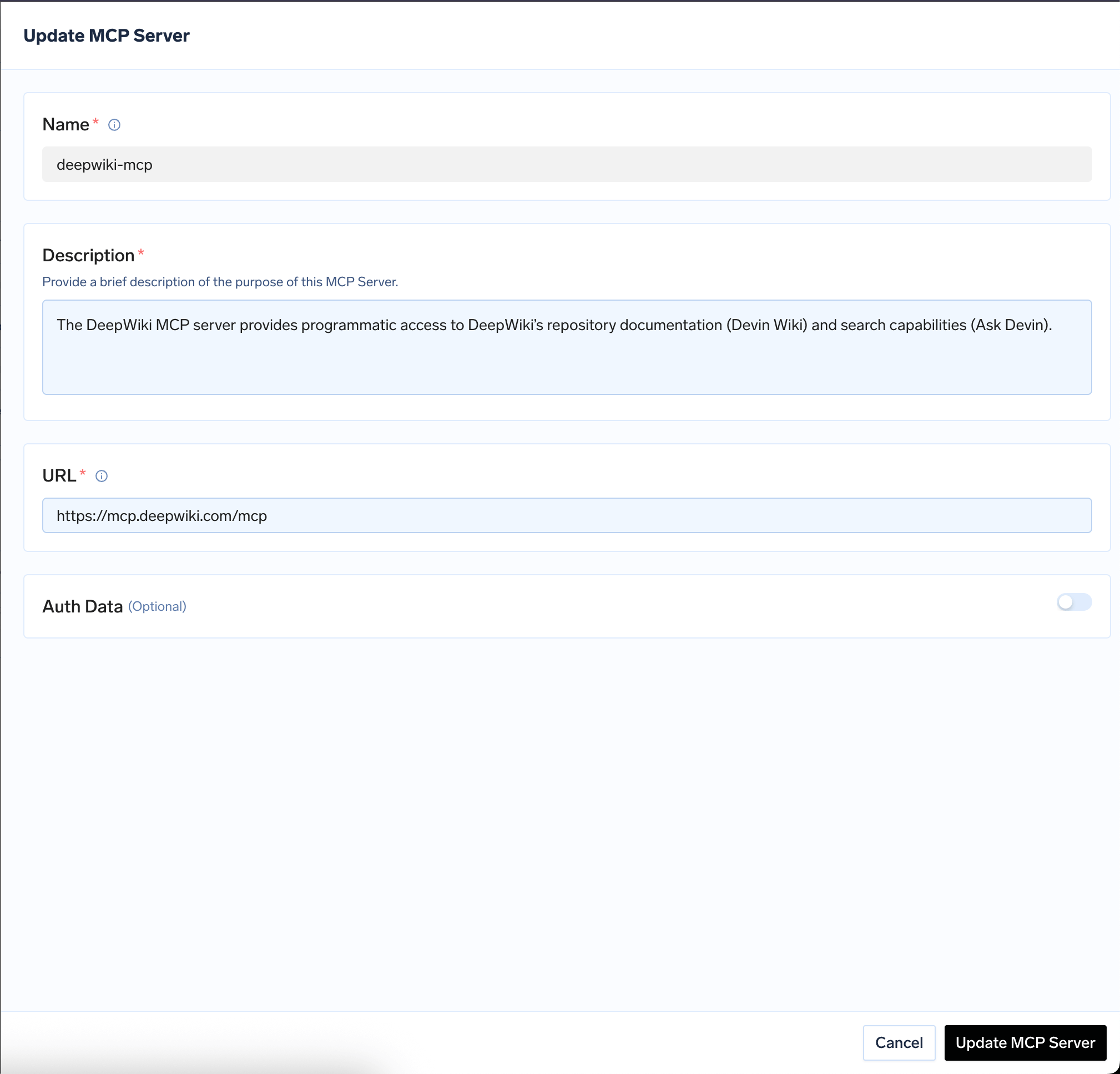
- Demo or sandbox APIs
- Public tools like a Calculator MCP Server or DeepWiki MCP server

Static Header Auth (Shared Credentials)
Static Header Auth (Shared Credentials)
OAuth2 (Per-User Credentials)
OAuth2 (Per-User Credentials)
Each user authenticates individually, and the MCP server grants access only to resources that user is authorized to use. OAuth2 is supported by popular services like Slack, GitHub, Atlassian, Google, and more.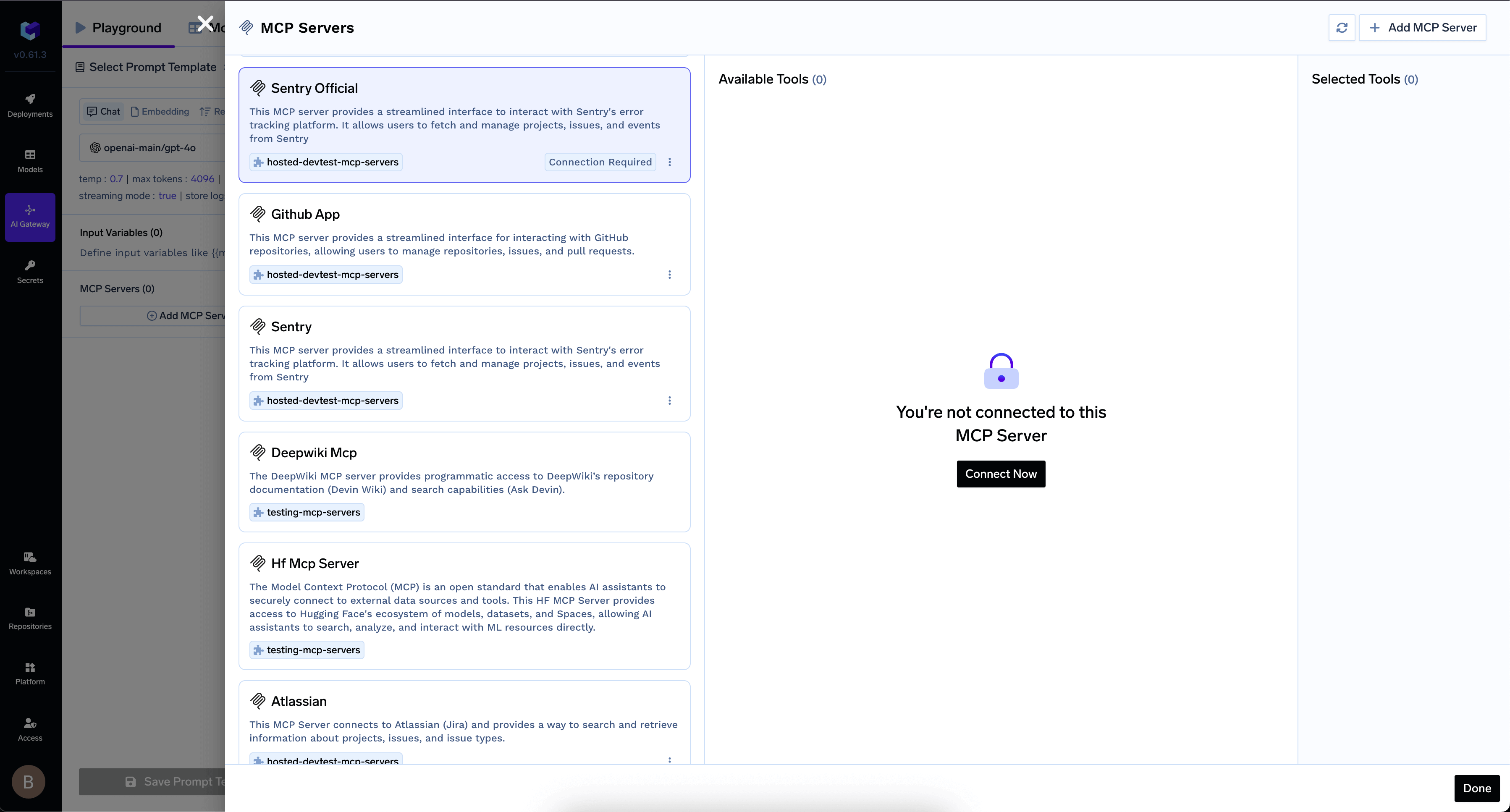
1
Create an OAuth2 app in your provider's developer portal
Set the redirect URI to:Replace
<tfy-control-plane-base-url> with your TrueFoundry control plane URL. Note your OAuth2 App ID, Secret, and required scopes.2
Register the MCP Server in the AI Gateway
-
Navigate to MCP Servers tab and click Add New MCP Server Group
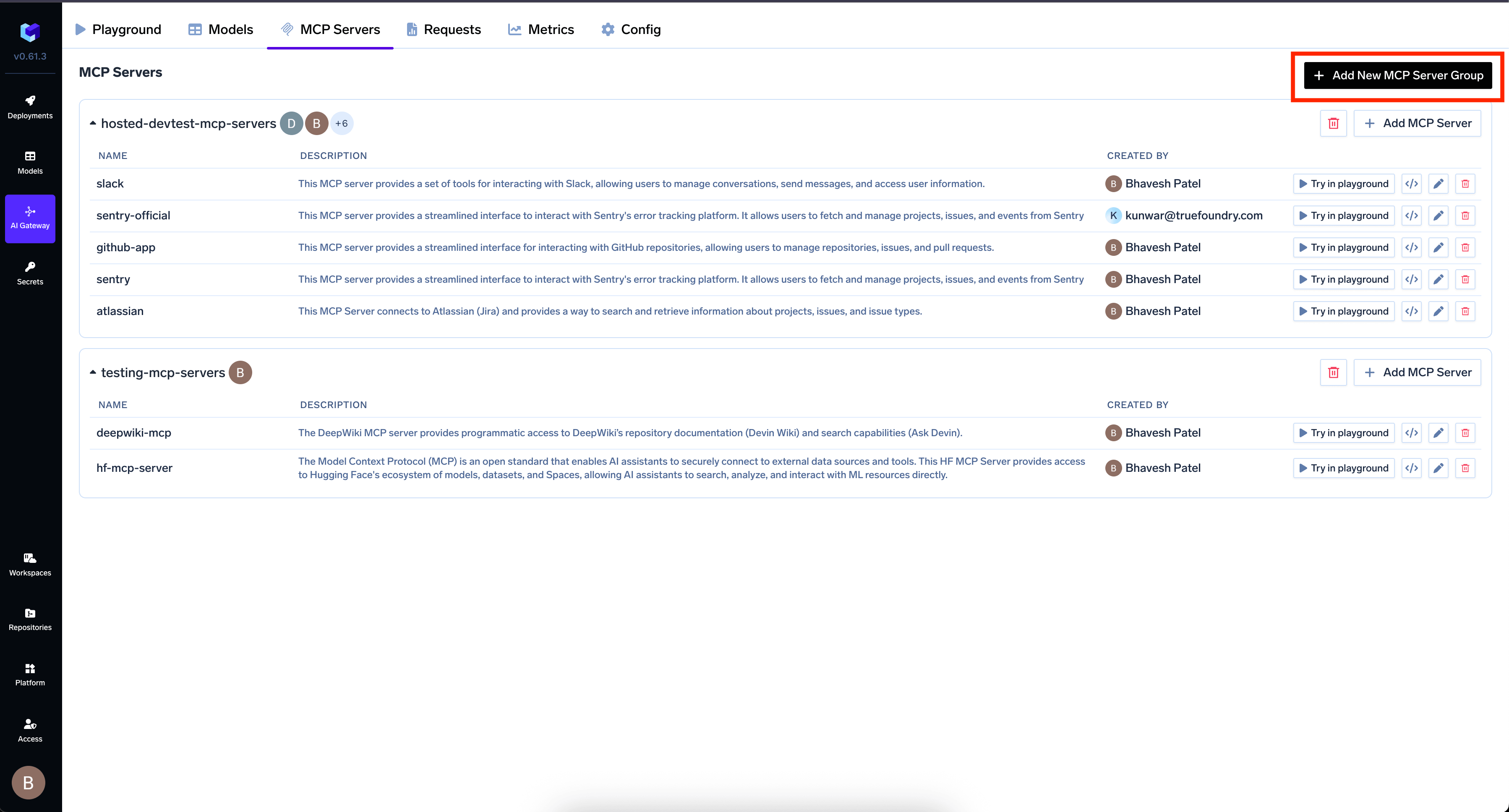
- Click Add MCP Server and provide:
- Endpoint URL: The URL of your MCP Server
- Authentication Type: Select OAuth2
- OAuth2 App ID: The client ID from your OAuth2 app
- OAuth2 App Secret: The client secret
-
OAuth2 App Scopes: Required scopes for accessing resources
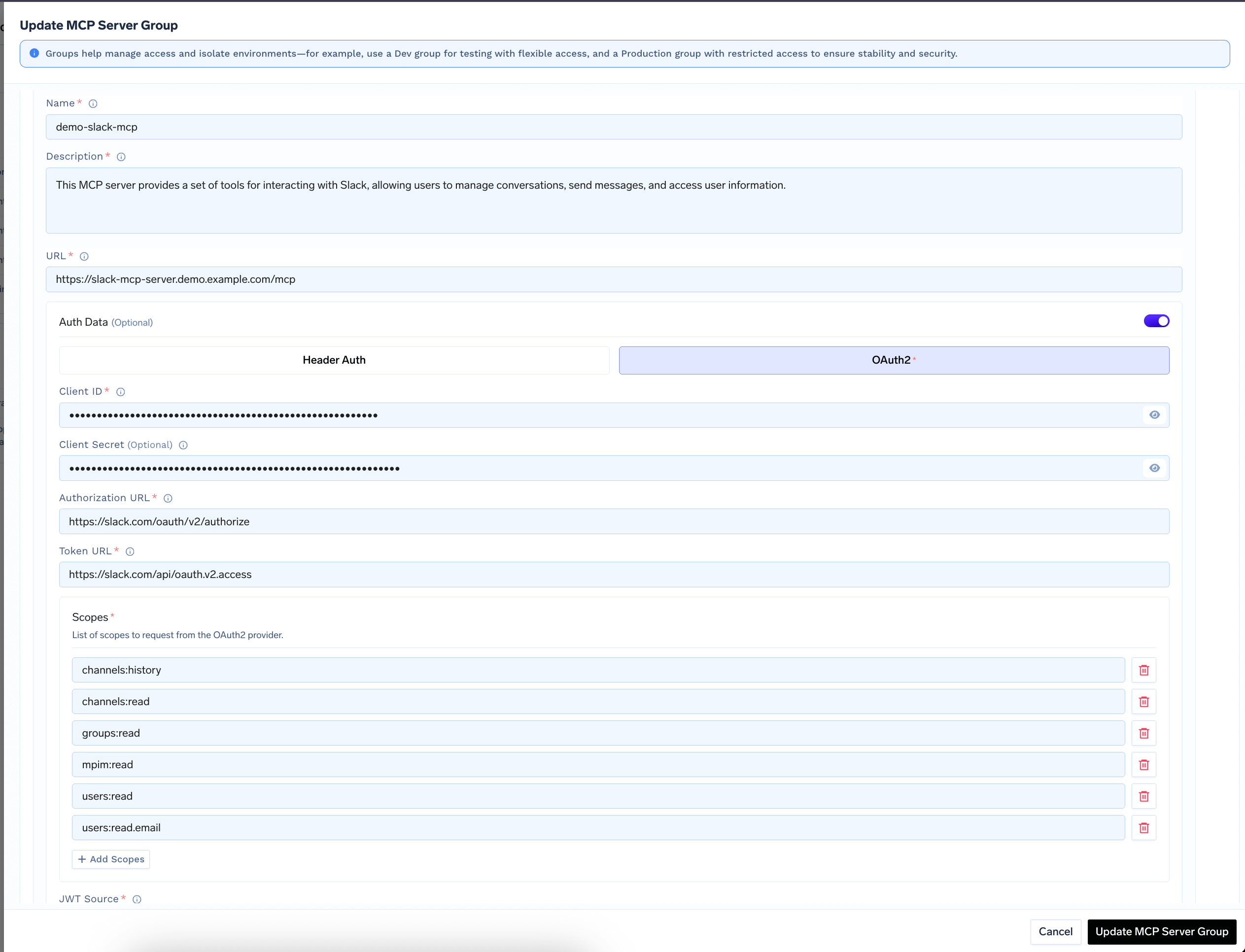
3
Connect and authorize
- Click Add Tool/MCP Servers in the AI Gateway UI
- For OAuth2 MCP Servers, click Connect Now to authorize

- Once authorized, the MCP Server’s tools appear in the list

- You can revoke authorization at any time:

Token Passthrough
Token Passthrough
The Gateway passes the user’s JWT directly to the MCP server without transformation. The MCP server validates the token itself.Configuration:
- Register the MCP server with Token Passthrough authentication type
- Configure an External Identity to allow your IdP tokens
- The user’s JWT is automatically forwarded to the MCP server
With Token Passthrough, the MCP server is responsible for validating the token. Make sure the MCP server is configured to trust your IdP.
2
Use MCP Server in Your IDE
Once you’ve added an MCP server, you can easily integrate it with your favorite IDE or AI coding assistant. Navigate to the MCP server details page and click on the How To Use tab.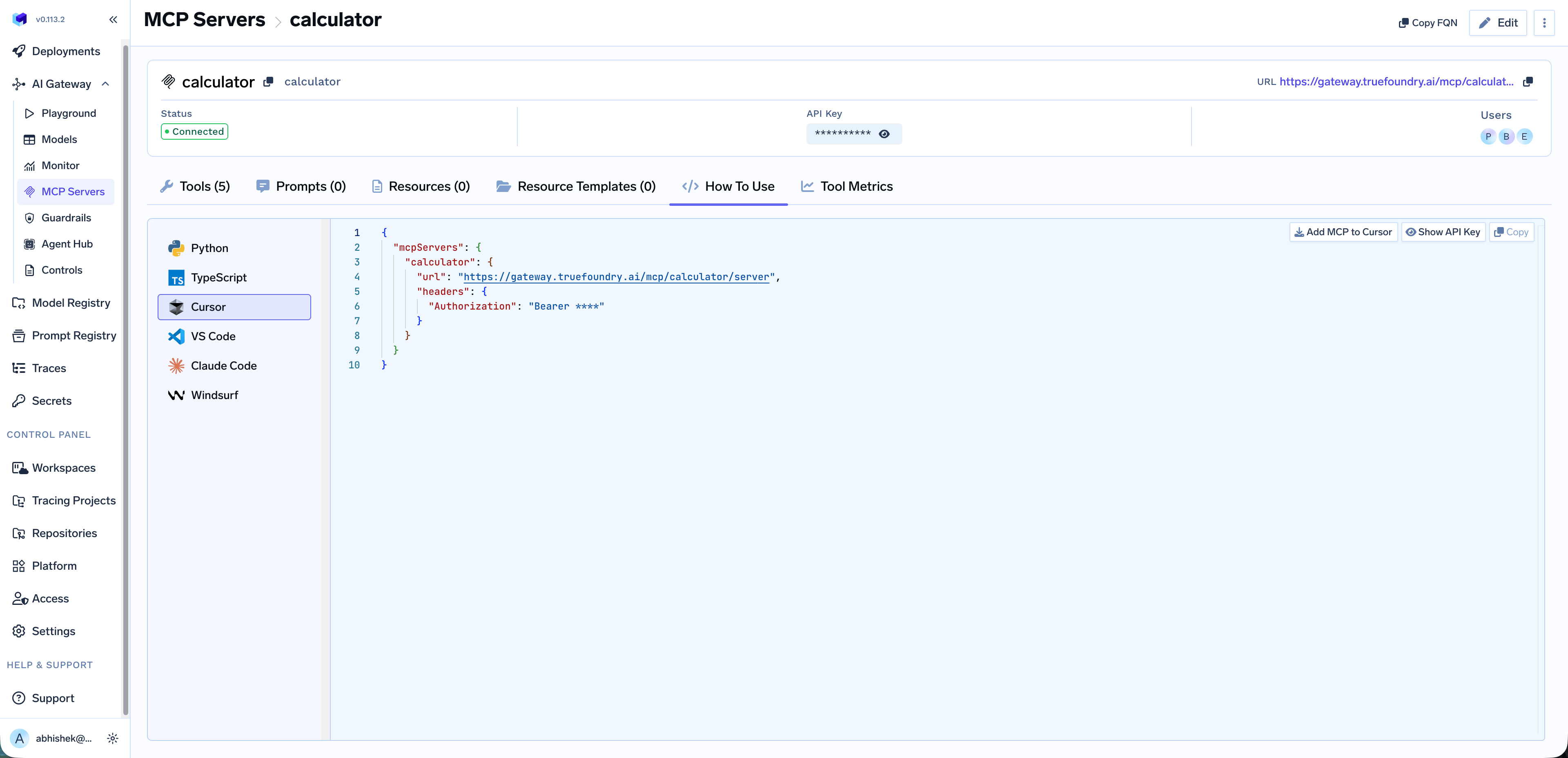

3
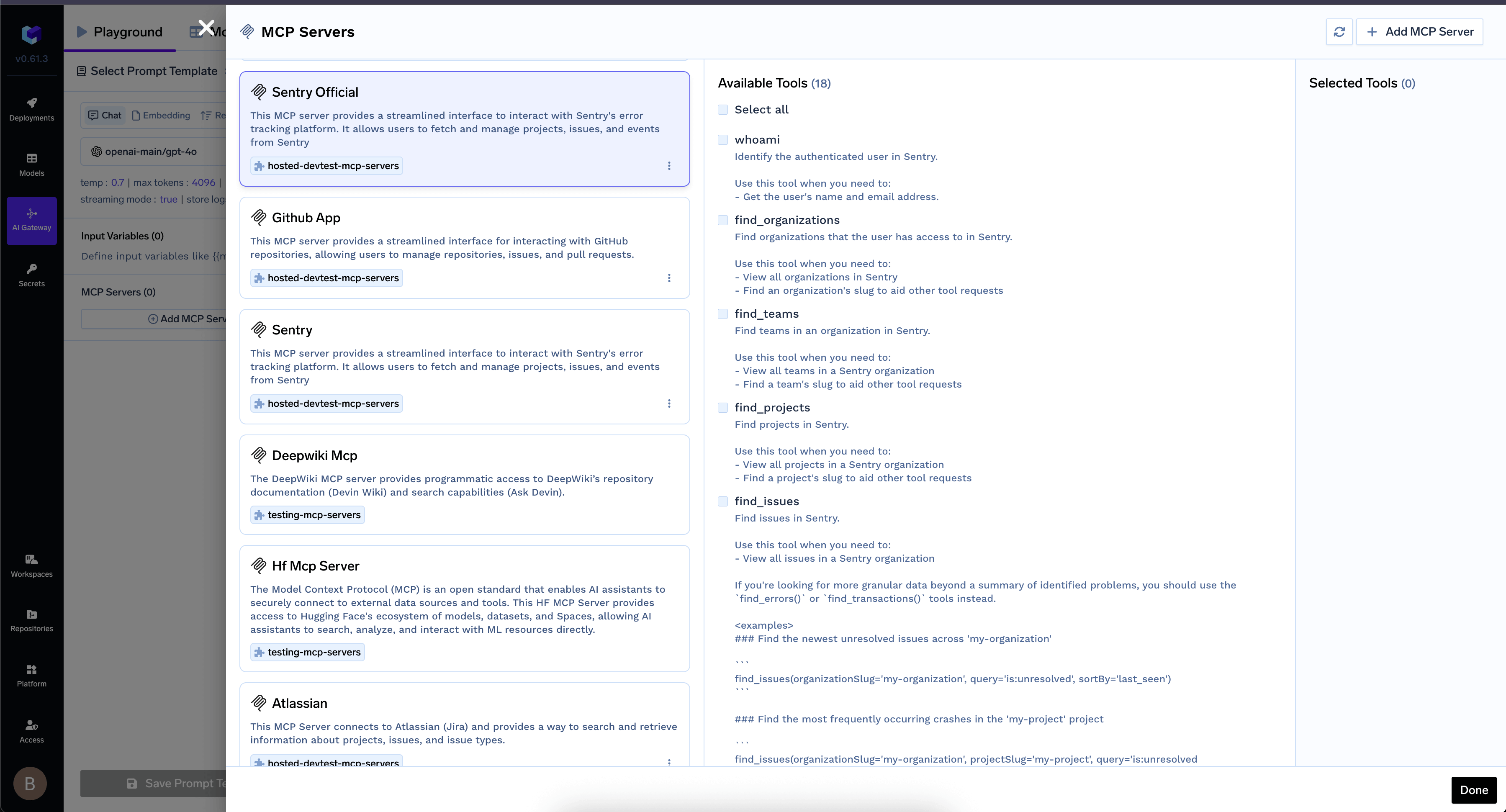
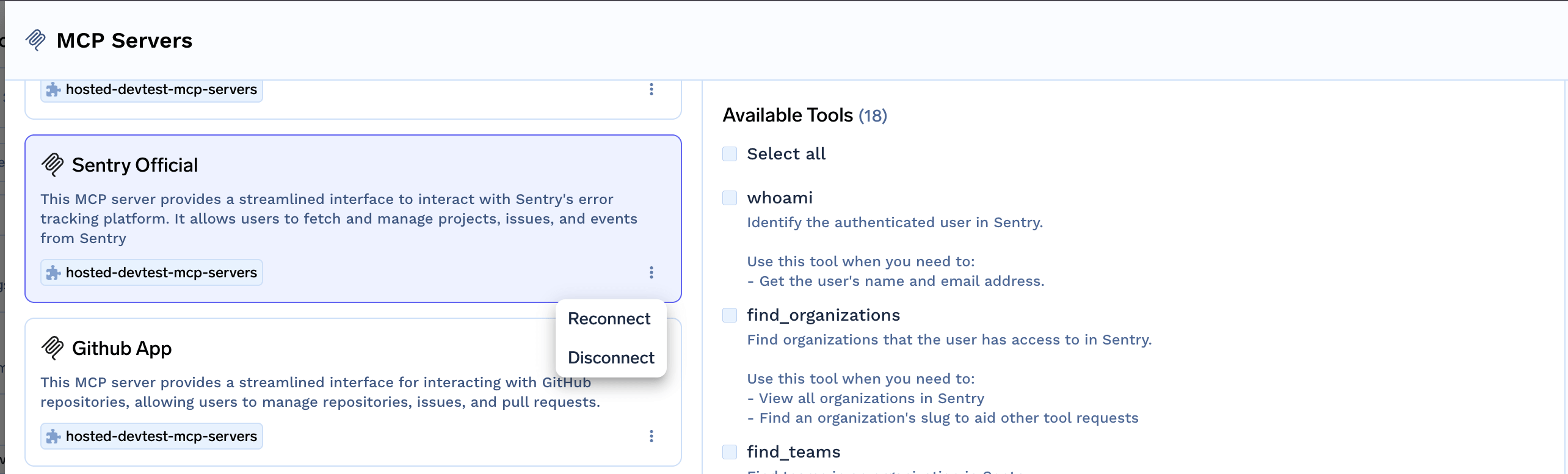
Use MCP Servers in Playground
You can select the MCP servers from the playground, select the tools and send your prompt to see which tools are being called.