Agent Gateway: Unifying Multi-Agent AI Workflows for Enterprises
Modern AI deployments increasingly use autonomous software agents that coordinate tasks across data sources and services. As these agentic systems scale, organizations face a new integration challenge: each agent may need to talk to many tools, APIs and LLMs, and without a central broker this leads to an “M×N” explosion of point-to-point connections. More critically, this creates “security blind spots” where developers scatter credentials and bypass governance.
An Agent Gateway is an emerging solution that sits between AI agents and their targets, providing a unified control plane for all agent communications. In practice, an Agent Gateway acts like a “traffic controller” for agent-to-agent and agent-to-tool messages, ensuring every request is authenticated, authorized, logged and routed correctly. By centralizing this layer – much as API Gateways did for web services – enterprises can scale multi-agent AI securely and efficiently.
What Is an Agent Gateway?
An Agent Gateway is a specialized API gateway built for AI agents – programs that autonomously plan and execute tasks (often using LLMs and external tools). Unlike a traditional API gateway (which simply proxies HTTP APIs) or even a standard AI/LLM gateway (which manages model endpoints), an Agent Gateway understands agentic protocols (like A2A and MCP) and multi-step workflows. In essence, it provides a single endpoint where all agents register and send their requests.
An Agent Gateway acts as the “central hub” in agentic AI systems – think of it as a traffic controller that keeps communications flowing smoothly and securely between autonomous agents. Similarly it can be described as a layer connecting, securing, and observing agent-to-agent and agent-to-tool communication across any environment. In short, the Agent Gateway abstracts the complexity of agent networks and tools behind one managed API, applying enterprise controls at every step.
Why We Need an Agent Gateway
As organizations build more sophisticated AI agents, the need for an Agent Gateway becomes clear.
First, there is a tool-integration explosion: each new agent might want to call multiple services (databases, APIs, LLMs, etc.), leading to a combinatorial spike in integrations. This is an “MxN integration problem” – connecting each of N agents to M tools scales poorly and slows development.
Second, out-of-the-box agent protocols (like MCP or Google’s A2A) are foundational but incomplete. They define how to serialize requests, but deliberately leave out critical enterprise concerns such as authentication, retries, routing and auditing. Without a gateway, each team ends up deploying and securing its own connectors ad-hoc – scattering API keys, creating shadow MCP servers, and generally inviting chaos. Gartner notes this “missing enterprise layer” problem: dozens of unmanaged MCP servers pop up, making it impossible to track which agent called what, and creating blind spots where sensitive data can leak.
An Agent Gateway solves these gaps by centralizing tool discovery and communication. It provides a single, unified interface so agents no longer need individual connections to each service – they simply talk to the gateway, which handles the rest. This centralization enables standard auth flows (OAuth, SSO), unified logging, rate limits, policy enforcement and more – bringing the same enterprise governance to agent workflows that already exists for web APIs.
Without an Agent Gateway, each agent would connect to tools individually (left), scattering keys and configs. With a Gateway (right), all agents use one entry point to discover and call approved tools under unified policies.
Key Features of an Agent Gateway
An effective Agent Gateway provides several core features to support secure, scalable agentic AI:
- Centralized Registry & Discovery: A catalog of approved agents and tools (MCP servers) managed in one place. Developers add tools once (with schemas or connectors) and all agents can find them dynamically through the gateway. This “single MCP endpoint” for all tools eliminates per-agent config.
- Authentication & Authorization: The gateway enforces identity checks on every request. It supports modern auth standards (API keys, OAuth2/OIDC, mutual TLS, etc.) so only legitimate agents or users can access specific tools. For example, TrueFoundry’s MCP Gateway lets you assign teams or OAuth2 client credentials to particular tool APIs, ensuring each agent can only call its authorized tools.
- Protocol Translation & Composition: Many AI tools speak different interfaces. The gateway can translate between protocols (e.g. converting an agent’s MCP JSON-RPC call into a REST API call or a Lambda invocation). It also composes multiple endpoints: an “API Composition” feature can merge several APIs or tools into one agent-facing endpoint for convenience.
- Routing & Load Management: Requests from agents are routed intelligently. The gateway can distribute calls across multiple backend servers (e.g. multiple LLM endpoints or tool replicas) for scalability. It handles session-affinity for streaming or Server-Sent Events protocols, ensuring the correct backend picks up two-way communication.
- Policy Enforcement & Quotas: Built-in policies regulate agent behavior. This includes rate limiting (requests per minute), token usage caps, budgeting and quotas per agent or team. It also enforces data governance rules: for example, blocking disallowed content or redacting PII from agent prompts as they enter the gateway. In short, policies ensure agents follow corporate rules even when they talk to external models.
- Observability & Auditing: Every interaction is logged and traced end-to-end. The gateway collects metrics on latency, error rates and usage (e.g. token counts, response sizes), and ties them back to specific agents or workflows. An admin can replay traces of multi-step agent conversations, debug failures, or audit exactly which agent invoked which tool with what data. This unified observability is crucial for compliance and debugging in complex AI systems.
- Security & “Guardrails”: Agent Gateways often implement safety checks. They can filter or transform content (e.g. sanitize inputs/outputs) to prevent hallucinations or malicious commands from propagating. For example, the gateway might inspect LLM responses and block outputs containing policy-violating content before returning them to an agent.
- Multi-Tenancy & Isolation: In large organizations, the gateway can isolate different teams or projects. Each team’s agents and tools can have their own namespace or virtual gateway instance, with separate credentials and quotas. This prevents inter-team interference while still reusing the central gateway infrastructure.
- Failover & Resiliency: An enterprise-grade Agent Gateway includes retries and fallback logic. If a tool or model endpoint fails, the gateway can retry or switch to a backup. This ensures robust agent execution even when individual components are unavailable.
Notably, many of these features mirror those of API or AI gateways, but in an agent context. TrueFoundry’s AI Gateway, for example, already provides a unified API key that lets users call all models and MCP tools they’re authorized for. This means agents need only one token to talk to any service through the gateway.

TrueFoundry also supports per-team RBAC on tools and even offers an Agent Playground where developers can interactively test prompts and orchestrate multiple tools via the gateway. These capabilities – centralized keys, team ACLs, built-in orchestration – are exactly the kind of governance benefits an Agent Gateway delivers.
Also explore: Top Agentic AI Platforms
How an Agent Gateway Works
Under the hood, an Agent Gateway operates as a reverse proxy tailored to agentic protocols. All agent requests are routed to the gateway first rather than directly to any service. For example, when an agent wants to invoke a tool, it sends a request (typically an MCP or A2A message) to the gateway’s endpoint. The gateway then:
- AuthN/AuthZ: Verifies the agent’s identity and checks permissions. It may decode an OAuth token or API key and confirm that this agent/user is allowed to call the requested tool.
- Routing & Protocol Handling: Based on the request content, the gateway looks up the target tool or LLM in its registry. It knows whether to connect to an internal MCP server, an external REST API, or an LLM service. The gateway may translate the request from one protocol to another (e.g. converting JSON-RPC to an HTTP API call). If multiple backends provide the same tool, the gateway balances or fans out the request accordingly.
- Orchestration (if needed): For multi-step workflows, the gateway can orchestrate calls to multiple backends in sequence or parallel. For instance, an agent’s single instruction might cause the gateway to first fetch data from one service, then pass results to another tool, and finally send the output back to the agent. In essence, the gateway can act as a lightweight workflow engine. TrueFoundry’s design, for example, explicitly “orchestrates the agentic loop between the LLM and the MCP servers”, streaming results through the LLM and toolchain.
- Streaming & Sessions: If a backend streams data (such as an LLM streaming tokens, or a tool emitting Server-Sent Events), the gateway maintains that stream back to the agent. The gateway keeps track of long-lived sessions so the agent receives updates as they occur. This is a key difference from stateless API proxies: an Agent Gateway tracks client sessions and can push responses or even initiate messages back to the agent when needed.
- Response Handling: Once the backend(s) respond, the gateway can apply response-time policies. It may redact sensitive information, enforce output schema validation, or trim large messages to save tokens. It then sends the final response back to the agent, possibly streaming it incrementally if it’s large or if the agent uses streaming.
- Logging & Telemetry: Throughout all steps, the gateway records each request and response. It attributes each call to the original agent, logs the sequence of calls, records latency, cost (token usage), and any policy violations. This trace data is stored so administrators can later audit or analyze the interaction.
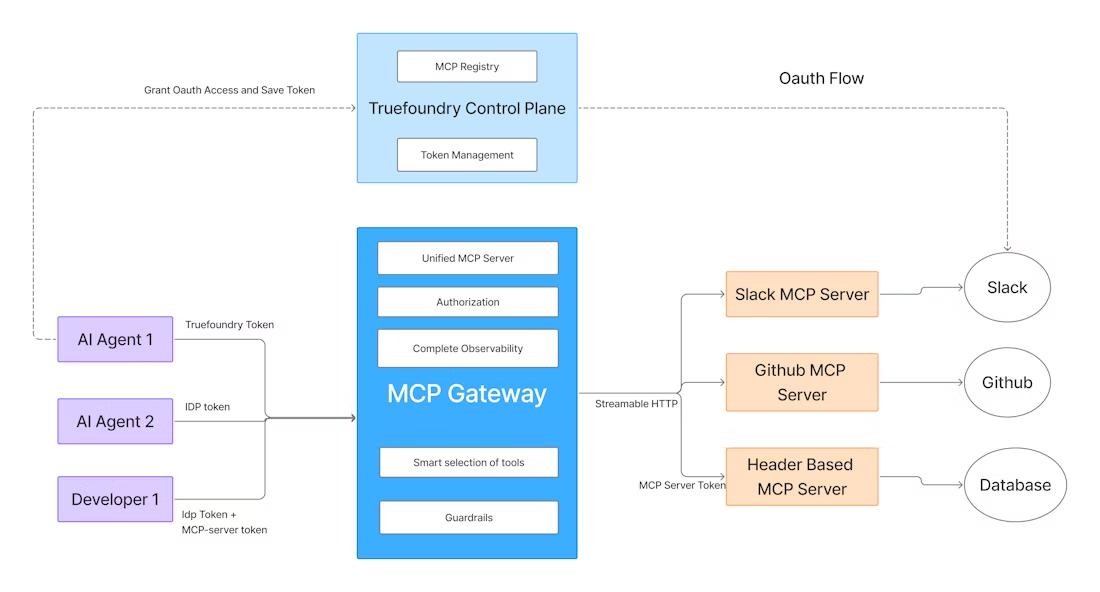
The diagram above (adapted from TrueFoundry’s docs) illustrates an MCP Gateway architecture.
Agents send requests into the gateway, which handles authentication, proxies calls to LLM models and tool servers (MCP), and then returns results. A central control plane manages registrations and access controls, while a built-in MCP client layer orchestrates multi-step calls between LLMs and tools.
Overall, the Agent Gateway acts as a stateful intermediary. By converting agent intents into concrete API calls and doing the reverse, it glues together autonomous agents, large language models, and traditional services into a cohesive, governed pipeline.Traditional API gateways cannot handle this natively – the Agent Gateway’s intelligence about JSON-RPC sessions, SSE streams, and MCP/A2A semantics is what makes it viable for real enterprise use.
Agent Gateway vs API Gateway vs AI Gateway
It helps to compare Agent Gateways to more familiar gateway types:
- API Gateway: A general-purpose gateway for web services (REST/gRPC). It handles routing, auth, rate-limiting, and caching for APIs. It is typically stateless (one request/response at a time) and does not natively understand LLM or agent protocol.
- AI Gateway: Often an extension of an API Gateway geared towards AI/LLM traffic. It adds features like multi-model routing, token usage tracking, prompt templating, and LLM-specific logging. For example, TrueFoundry’s AI Gateway lets developers call hundreds of LLM models through one endpoint with full access control and observability. It optimizes how applications interact with language models but usually still treats requests as independent calls.
- Agent Gateway: Takes the concept further to the agentic domain. It incorporates all API and AI gateway features plus special support for multi-agent workflows. This includes session-awareness (MCP/A2A), tool orchestration, and inter-agent message routing. In other words, an Agent Gateway is an AI Gateway on steroids for agents: it not only manages LLM calls, it also manages calls between agents and tools in multi-step chains. As Gravitee explains, AI Gateways and Agent Gateways are separate but complementary – the Agent Gateway focuses on agent-to-agent communication under governance, whereas the AI Gateway focuses on LLM interactions with the broader system. Solo.io similarly emphasizes that while MCP/A2A define low-level RPC, only an Agent Gateway provides the “enterprise-grade security, resilience, observability, and multi-tenancy” layer needed.
In practice, the boundaries blur. Many platforms (including TrueFoundry) are converging these concepts. TrueFoundry’s platform, for instance, already offers a unified AI Gateway that covers models, hybrid GPU/MCP servers, and (soon) agents. But conceptually, think of an Agent Gateway as a specialized gateway focused on coordinating agents rather than just serving models or microservices. It applies similar governance (authz, quotas) across agentic workflows.
Common Use Cases of Agent Gateways
Agent Gateways enable a variety of advanced AI applications. Examples include:
- Multi-step Automation Workflows: Complex tasks that require several AI steps. For instance, an enterprise might create a “support ticket” workflow: one agent reads customer emails, another queries a knowledge base (via the gateway’s tools) to draft responses, and a third calls a ticketing API to log the issue. The Agent Gateway logs each call and ensures only approved actions occur. TrueFoundry illustrates such a flow: a “Planner” agent interprets a Slack command, calls a Slack MCP tool, a “Summarizer” agent processes the data, and an “Executor” agent creates Jira tickets – all through a centralized gateway which secures each step.
- Tool-Assisted QA and RAG: Retrieval-augmented generation often uses one or more LLMs plus external tools (search engines, databases). An Agent Gateway can present all these search and database tools as MCP services, letting an LLM or agent agentically fetch and combine information under policy. For example, an AI agent answering medical queries could retrieve licensed medical data (as MCP tools) through the gateway, while content filters and audit logs ensure compliance.
- Intelligent Assistants with Function Calls: Modern chatbots (like OpenAI’s function-calling chat models) effectively act as agents calling APIs for functions like “bookFlight” or “scheduleMeeting.” An Agent Gateway can serve as the function-call interface, mapping these agentic calls to real booking or calendar APIs with enterprise auth. This offloads credential management and logging to the gateway.
- DevOps and IT Automation: Agents can automate software pipelines by calling various APIs (GitHub, CI/CD, cloud consoles). An Agent Gateway unifies these calls: an agent with natural-language intent (“deploy the latest commit if tests passed”) is routed to the correct APIs behind the gateway, and each API key is managed centrally.
- Data Pipeline Orchestration: One agent might cleanse data, another analyzes it, another visualizes it – all using specialized tools. The gateway ensures they chain together correctly. For instance, a data analytics agent could query a database via an MCP tool, then hand off to a reporting agent that formats the results, all under single-agent workflow governance.
- Low-Code Agent Platforms: The gateway extends easily to end-user agent builders. TrueFoundry’s blog shows that low-code flows created with Flowise can be quickly pointed at the gateway: once the gateway URL and token are entered, “every LLM call now flows through the Gateway,” instantly inheriting centralized governance like cost tracking, observability, and security. This means that experimental agents (even drag-and-drop ones) benefit from production-grade controls as soon as they go through the Agent Gateway.
In all cases, the Agent Gateway provides the glue and guardrails that make agentic AI enterprise-ready. It ensures that whether an agent is a custom app or a third-party bot, it uses the organization’s sanctioned models and tools, stays within budget, and generates a full audit trail.
Challenges in Agent Gateway Adoption
While powerful, Agent Gateways also introduce new considerations:
- Protocol Complexity: Agent protocols like MCP are stateful and bidirectional, which is very different from typical REST APIs. Gateways must handle multiple open connections per session, multiplex Server-Sent Events, and preserve JSON-RPC context. This complexity requires a purpose-built implementation (Solo chose Rust, for example) rather than repurposing a generic API proxy.
- Scalability and Performance: Keeping live sessions for many agents can tax resources. The gateway must be highly performant to avoid introducing latency. It often needs to cache or trim responses to reduce token usage for costly LLM calls.
- Security of Autonomous Agents: Agents can potentially be manipulated to access unauthorized data or perform malicious actions. Ensuring comprehensive guardrails in an agentic flow is challenging. The gateway must validate not just initial requests but also intermediate outputs between agents, which can be complex.
- Operational Complexity: Adding a new gateway service (and the dependencies it needs) increases infrastructure complexity. Teams must manage high availability, monitoring and updates for the gateway itself, on top of their existing AI stack.
- Standardization and Maturity: Agent protocols like MCP and A2A are relatively new (MCP was launched late 2024) and still evolving. The ecosystem of agent frameworks and tools is nascent. Early adopters may face version mismatches or lack of support from some vendors. Integrating legacy APIs (that were never designed as “agent-native” tools) may require custom adapters or wrappers.
- Debugging Multi-Agent Flows: While the gateway provides observability, reasoning about multi-agent interactions across different tools can still be non-trivial. Tracing an agentic conversation end-to-end requires robust tools and potentially new skillsets for development teams.
- Cost Management: Interestingly, an Agent Gateway can both help and complicate cost tracking. It centralizes usage metrics, but with many agents and providers, accurately attributing usage (especially across chained calls) requires careful design.
Despite these challenges, the industry consensus is that Agent Gateways address more problems than they create. In fact, Gartner explicitly calls them the “missing layer” for secure AI integration. As adoption grows, we can expect these gateways to become standard components of AI infrastructure, much as API gateways did for microservices.
How to Get Started with an Agent Gateway
Organizations eager to adopt an Agent Gateway have several paths:
- Evaluate Open Source Projects: Solo.io’s agent gateway (now a Linux Foundation project) is a community-driven gateway with connectors for A2A and MCP protocols. It provides a tool federation portal and developer UI for creating agentic workflows. Experimenting with this project can give teams hands-on insight into agent gateway patterns.
- Leverage AI Gateway Platforms: Platforms like TrueFoundry already incorporate agent gateway functionality. While the dedicated Agent Gateway feature is “coming soon”, TrueFoundry’s existing AI Gateway supports MCP tool registration and agent-friendly APIs. You can sign up for TrueFoundry’s platform (free trial, no credit card) and follow the quick-start guides to connect LLMs and MCP tools. TrueFoundry’s docs walk through setting up the Gateway UI, adding model providers, and even adding MCP servers as tools. Using these steps, developers can start building simple agents (e.g. via Flowise or custom code) that automatically use the Gateway’s managed endpoints.
- Use Agent-Friendly Tools: If you’re building agents with frameworks like LangChain, LlamaIndex or Flowise, look for features to point their output to a custom endpoint. As TrueFoundry demonstrated, simply configuring a low-code agent to use the Gateway’s API URL can bring all agent traffic under the gateway’s control. Similarly, open-source agents supporting MCP can register their MCP servers via the gateway’s API and then start invoking them through the centralized interface.
- Adopt Identity and Governance Early: Since an Agent Gateway hinges on centralized auth, integrate it with your corporate identity (SSO/OAuth) from day one. For example, TrueFoundry lets you use standard OAuth2 (2LO/3LO) for both users and services. Configure these flows early to avoid last-minute security gaps. Also define your RBAC and policy requirements in advance – the sooner they are codified in the gateway, the smoother scaling will be.
- Learn from Examples and Tutorials: TrueFoundry’s documentation and blogs are useful resources. The “Flowise Agent” tutorial covers building an agent behind the gateway step-by-step. The TrueFoundry docs include a “Playground” for testing MCP tools and code snippets for invoking them via the gateway. Beyond TrueFoundry, the Solo.io and API/AI gateway communities (e.g. Apache APISIX with AI plugins) provides guidance on architecture and best practices.
By starting small – for instance, exposing one internal API as an MCP server in the gateway and testing an agent flow – teams can build confidence. Over time, they can migrate more agents to use the centralized gateway endpoint, systematically unlocking the benefits of unified governance and monitoring. The key is to treat the Agent Gateway as the integration point: any new agent or tool should go through it by default.
Conclusion
Agent Gateways represent a new frontier in AI infrastructure, one that aligns agentic innovation with enterprise requirements. They bring the same kind of central management to multi-agent systems that API gateways brought to microservices. By unifying agent communications, enforcing policies, and providing full observability, an Agent Gateway turns sprawling, ad-hoc agent networks into a disciplined, secure workflow.
For organizations deploying AI at scale, this layer is quickly becoming indispensable. As Gartner observed, it fills a “missing layer” in the stack. Products like TrueFoundry’s AI Gateway are already moving in this direction (with an Agent Gateway module on the way) to ensure that developers and CTOs can build with agents confidently rather than chaotically.
In the emerging era of multi-agent AI, the Agent Gateway is the bridge between cutting-edge automation and reliable production operations. Embracing it can dramatically simplify AI rollout: teams no longer need to reinvent integration code or compromise on security for the sake of agility. Instead, they gain a single pane of glass for all agent work – one that enables innovation and control to flourish together.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.






.jpg)












