How to build an ITAR Compliant AI Gateway?
ITAR, or the International Traffic in Arms Regulations, is a set of U.S. government regulations administered by the Department of State’s Directorate of Defense Trade Controls (DDTC). Its core purpose is to control the export and handling of defense-related articles, services, and technical data listed under the United States Munitions List (USML).
Put simply, ITAR governs how sensitive military technologies and information are accessed, shared, and transferred – especially across national borders. This includes not just physical products like weapons or aircraft components, but also digital assets such as design files, software code, or technical documentation that could be used in the development or maintenance of defense systems.
Some key requirements of ITAR include:
- U.S. Person Access: Only individuals who are U.S. citizens, lawful permanent residents, or authorized under specific exemptions can access ITAR-controlled data.
- Data Residency: Controlled technical data must remain on U.S. soil unless an export license has been granted.
- Export Restrictions: Any transmission (including cloud access) of ITAR data to foreign entities or locations is considered an export and is tightly regulated.
Violations can lead to severe penalties, including fines in the millions of dollars, criminal charges, and loss of export privileges. As AI tools become more integrated into sensitive industries like aerospace, defense, and intelligence, ITAR compliance becomes critical in the design and deployment of any system – especially AI gateways that process technical data.
What Is an ITAR-Compliant AI Gateway?
A generative AI gateway is essentially a model-aware API proxy for AI services. It understands AI-specific concepts like token usage, content filtering, and multi-model routing. It centralizes policy enforcement: for example, it inspects every AI prompt and response for sensitive content (blocking or redacting as needed) and enforces token quotas and rate limits per user or team. It also routes requests to the optimal model or data center (e.g. switching between OpenAI, Anthropic, on-prem models) based on cost, performance, or policy rules.
An ITAR-compliant AI gateway extends this idea by adding controls required under the International Traffic in Arms Regulations. In short, ITAR compliance means following U.S. State Department regulations on the export and handling of defense-related technical data. This includes keeping all controlled data within approved U.S. jurisdictions and limiting access to U.S. persons. Thus an ITAR-compliant AI gateway ensures that any AI model call that involves ITAR-controlled information is subject to these restrictions. For example, it may block queries that would send protected technical data to unapproved foreign servers, encrypt traffic end-to-end with keys held in the U.S., and integrate with identity management to verify the user’s citizenship. In effect, it acts like a secure “checkpoint” for AI traffic – much as airport security inspects passengers and luggage, the ITAR gateway inspects and governs AI requests. An AI gateway becomes your organization’s AI firewall by bringing visibility and compliance controls to every AI interaction.
Why an ITAR-Compliant AI Gateway Matters
Enterprises handling defense or aerospace technology must comply with ITAR or face severe penalties. Violating ITAR can result in hefty fines, imprisonment, and loss of export privileges. Even well-intentioned AI usage can inadvertently breach ITAR: for instance, if an engineer accidentally sends proprietary military blueprints as a prompt to a foreign AI API, that would be an unauthorized export of technical data. In regulated sectors, ITAR compliance is not optional – it is often required to win and maintain government contracts.
An ITAR-compliant AI Gateway matters because it enables organizations to leverage generative AI safely within these legal bounds. It prevents sensitive data from “leaking” outside approved channels. For example, by enforcing U.S.-only data residency and checking user identity, the gateway ensures that no ITAR data ever leaves the U.S. or is seen by foreign nationals. It also provides an audit trail: every AI request and response is logged for forensic review, which is crucial for demonstrating compliance to regulators. In short, the gateway makes it possible to use advanced AI models while satisfying ITAR’s end-to-end security requirements. As highlighted by industry experts, for multi-provider, regulated AI workloads the solution is to deploy a specialized gateway control plane that enforces policies like token budgets, content safety, and “data-residency enforcement”. Without this control layer, enterprises risk uncontrolled AI usage that could violate ITAR and compromise national security.
Key Requirements of ITAR Compliance in AI Gateways
To be ITAR-compliant, an AI gateway must incorporate all of the data protection and access controls that ITAR mandates for defense-related technology. Key requirements include:
- Strict Access Controls: Only authorized U.S. persons may access ITAR-controlled data. This means integrating with corporate identity systems (e.g. SSO/AD) and enforcing multi-factor authentication and role-based permissions. Any request from an unvetted or foreign user must be blocked.
- Encryption (In Transit & At Rest): All sensitive data passing through the gateway must be encrypted end-to-end. This includes encrypting API requests and responses over TLS, and encrypting stored data (e.g. logs) at rest. Often this requires customer-managed keys or hardware security modules that remain in the U.S.
- U.S. Data Residency: The gateway and all processing (including model inference and logging) must occur in approved U.S. facilities or cloud regions. In practice, this means running the gateway on-premises or in a US-based government cloud, and only invoking AI models that operate in U.S. regions.
- Detailed Audit Logging: ITAR requires comprehensive record-keeping. The gateway must log every query, response, user identity, and timestamp. These logs should be securely stored and easily auditable. (“Travel logs are maintained” – every AI interaction is recorded for compliance review.)
- Content Filtering: The gateway should detect and prevent the export of controlled technical data. For instance, it can block prompts or outputs that contain defense design details or classified terms. This content moderation acts like airport security scanning for prohibited items.
- Organizational Best Practices: Beyond the technical measures, best practices include regular employee training on ITAR rules and maintaining a culture of compliance. Companies should establish incident response and regular audit procedures to ensure the gateway’s policies are up to date.
By meeting these requirements, an AI gateway creates a secure environment where defense-related AI workloads can be performed without risking an ITAR violation.
Design Considerations for ITAR-Compliant AI Gateways
Building an ITAR-compliant gateway involves careful architectural design. Key design considerations include:
- Deployment Environment: The gateway should run in an approved infrastructure. Many organizations opt for an on-premises or air-gapped deployment, or use a U.S. government cloud region (e.g. AWS GovCloud or Azure Government) that is certified for ITAR and FedRAMP. This ensures the physical and jurisdictional security of data.
- Network and Data Isolation: The design should segment the gateway from public networks. All traffic to AI providers should go through the gateway only. Outbound connections should be restricted so that data cannot flow to unauthorized endpoints. Using Virtual Private Clouds (VPCs) with strict firewall rules is common.
- Key Management: Encryption keys used by the gateway must be under customer control. Often, this means integrating with a U.S.-based Hardware Security Module (HSM) or KMS so that keys never leave U.S. soil. This protects against any foreign access to decrypted data.
- Identity and Access Management: The gateway needs to integrate with corporate IAM systems (LDAP/AD, OAuth, etc.) to enforce user eligibility. In a federated environment, gateways may need to check attributes like citizenship or security clearance flags before granting access.
- Logging Architecture: The gateway should be designed so that logs and analytics also stay within the secured environment. For example, rather than forwarding logs to an external SaaS analytics service, a gateway can be built to write logs to an in-network database or object store. This preserves data sovereignty.
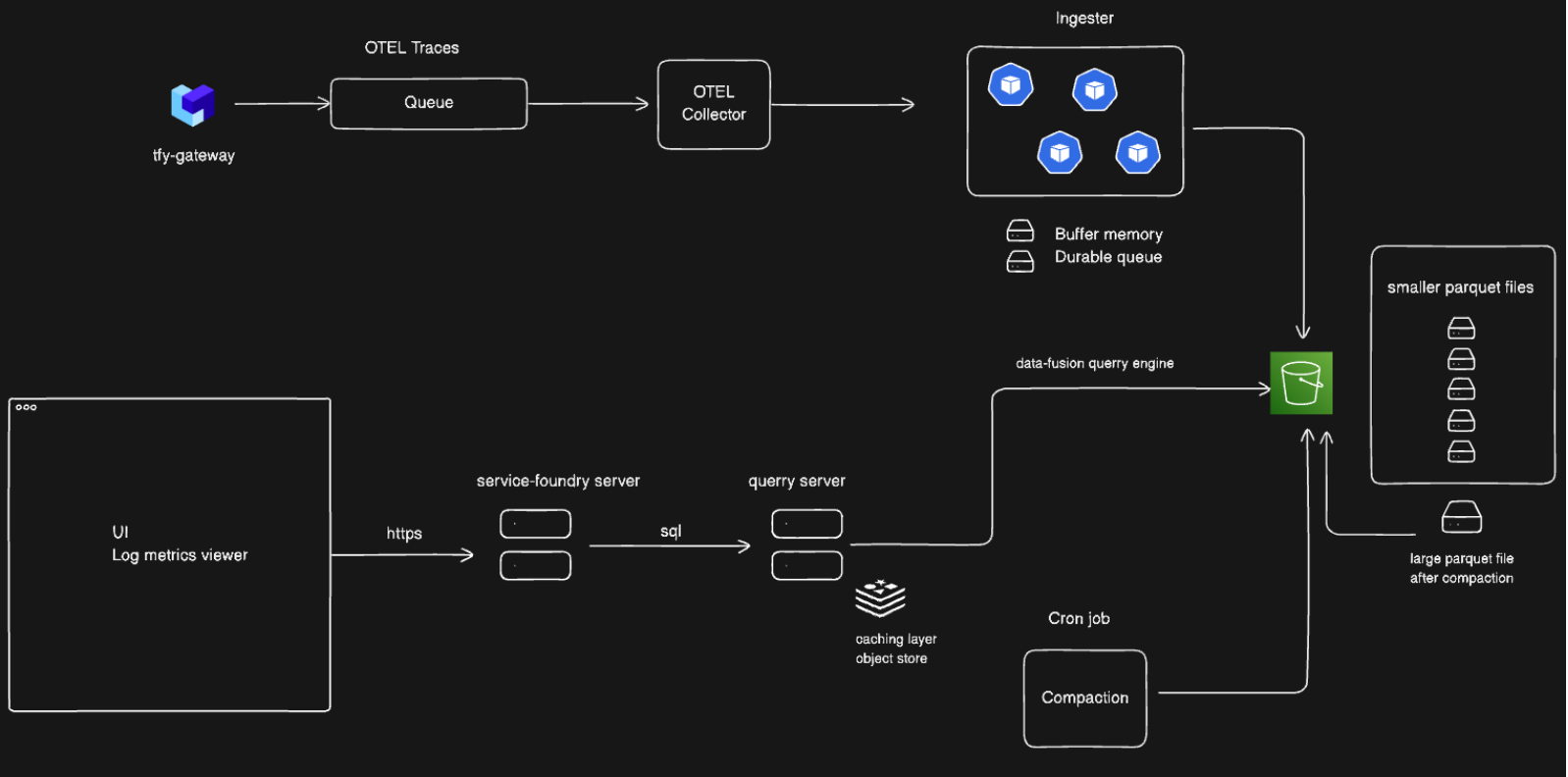
TrueFoundry’s architecture, for instance, decouples analytics so that all logs remain in the customer’s control plane
- Model Access Policies: Not all AI models will meet ITAR requirements. The gateway design should allow selecting only approved models. For example, if using a cloud LLM, ensure it is served from U.S. data centers and that the provider signs a Data Processing Addendum covering ITAR. The gateway can enforce a whitelist of model endpoints.
- Performance and Resilience: Encryption and content filtering add latency. The design should account for these overheads, perhaps by autoscaling the gateway or using high-performance hardware. Redundancy and failover are also important (the gateway is on the critical path for all AI calls).
- Security Hardening: Standard measures like intrusion detection, secure boot, and vulnerability scanning should be applied to the gateway software. An attacker should not be able to exploit the gateway to leak data.
Each of these design choices helps ensure that the gateway enforces ITAR rules by architecture. For example, by keeping all components inside U.S. boundaries and under strict control, the gateway fulfills the ITAR requirement of “data residency within the U.S.”. By tying into corporate identity, it enforces the requirement of “only authorized U.S. persons”. In practice, the gateway’s architecture must treat sensitive data with the same care as any classified defense system.
Core Capabilities of an ITAR-Compliant AI Gateway
An ITAR-compliant AI gateway provides a rich set of security and management capabilities tailored for regulatory compliance. Core features include:
- Secure Access & Authentication: Integrates with enterprise identity (LDAP/AD, SSO) and IAM, ensuring only authenticated, authorized users (verified as U.S. persons if needed) can use the AI APIs. Supports multi-factor authentication and fine-grained permissions.
- Content Moderation & Filtering: Scans every AI prompt and generated response for disallowed content. This can include military technical terms, personal data, or any classified information. Risky outputs are blocked or redacted before reaching the user.
- Multi-Model Routing: Routes requests to the appropriate AI models or endpoints. For ITAR use-cases, the gateway can be configured to send requests only to approved on-prem models or cloud models hosted in U.S. regions. It can fail over to backup models transparently.
- Usage Governance: Enforces quotas and rate limits on AI usage. The gateway tracks token consumption per user, project, or department, and can throttle or shut off traffic that exceeds policy limits. This prevents runaway queries and helps control costs.
- End-to-End Encryption: All communication through the gateway is encrypted. The gateway uses customer-managed keys for TLS and data encryption, ensuring that even the gateway operators cannot read plaintext sensitive data.
- Comprehensive Logging & Auditing: Every API call and model response is logged in detail. Logs include metadata such as user identity, timestamps, full prompts, and outputs. These logs are stored securely (e.g. in encrypted storage) for later audit or investigation. The gateway often provides dashboards or integrations to monitor compliance in real time.
- Policy Enforcement Engine: The gateway can apply complex policy rules to each request. For example, it can automatically redact PII from outputs, block certain prompt categories, or require approval for sensitive queries. Policy updates take effect immediately across the organization.
- Observability and Alerting: The gateway includes monitoring of its own health (latency, errors) and data flows. It can alert administrators if unusual patterns occur (e.g. a spike in queries or a policy violation attempt), so that compliance teams can respond quickly.
Together, these capabilities transform the gateway into a one-stop control point for all AI-related risks. As TrueFoundry describes, the gateway essentially acts like an AI “control tower,” making informed decisions about which model to call, how to handle outputs, and how to enforce security for every AI interaction.
In an ITAR context, each of these core functions is aligned with compliance: strict access control and encryption protect data, content filters prevent forbidden exports, routing choices ensure U.S. hosting, and logs provide the audit trail mandated by law.
Implementation Checklist & Best Practices
Successfully rolling out an ITAR-compliant AI gateway involves both technical steps and governance processes. Below is a checklist of key actions and best practices:
- Identify ITAR Scope: Catalog all AI-related data and use cases to determine what is ITAR-controlled (e.g. defense designs, military software code). Classify these assets according to the U.S. Munitions List.
- Register and Plan: Ensure the organization is registered with the DDTC (Defense Trade Controls) if required, and that there is a written ITAR compliance plan. While not specific to the gateway, regulatory registration is a foundational step.
- Select the Environment: Choose a deployment environment that meets ITAR requirements. For example, deploy the gateway in a U.S.-only cloud region or on-premises enclave. Configure the VPC/network so that no traffic can bypass the gateway.
- Implement Encryption and Key Management: Use strong encryption for all data flows. Store TLS certificates and encryption keys in a secure vault or HSM (Hardware Security Module) within the U.S.. Ensure databases or storage buckets for logs are also encrypted and in approved locations.
- Integrate Identity Controls: Connect the gateway to corporate identity providers (e.g. LDAP, Okta). Define user groups that map to ITAR-clearance roles. Set up SSO and enforce strict authentication (MFA) for gateway access.
- Configure Gateway Policies: Define the actual AI usage policies in the gateway. This includes whitelisting approved model endpoints (e.g. self-hosted LLMs or specific cloud AI services), setting content filtering rules (e.g. block any output matching military keywords), and specifying quotas.
- Enable Logging & Monitoring: Turn on detailed request/response logging. Verify that logs capture all required fields and are written to secure, access-controlled storage. Set up dashboards or SIEM alerts to monitor gateway activity for anomalies.
- Conduct Testing and Validation: Simulate common use cases (and misuse cases) to test the gateway. For example, attempt to send a sensitive prompt or connect as an unauthorized user, and confirm the gateway blocks it. Perform a security review or penetration test on the gateway.
- Train Users and Administrators: Educate AI users and platform operators about the new gateway. Ensure developers know to route all AI calls through the gateway and understand ITAR basics. Provide compliance training so that staff know the importance of these controls.
- Maintain and Audit: ITAR compliance is ongoing. Regularly audit logs and policies. Update the gateway rules as regulations or business needs change. Document all compliance activities in case of an inspection.
Following this checklist helps ensure that the technical deployment aligns with ITAR’s procedural requirements. For example, strict access and encryption practices address “key ITAR cybersecurity requirements” like limiting access to authorized personnel and encrypting data in transit and at rest. Training and audit steps fulfill ITAR’s demands for a compliance culture. In effect, the gateway implementation becomes part of the organization’s overall ITAR compliance program.
Challenges in Deploying ITAR-Compliant AI Gateways
Implementing an ITAR-compliant gateway is not without difficulties. Some of the main challenges include:
- Regulatory Complexity: ITAR regulations are detailed and often open to interpretation. Deciding whether a particular piece of data or model output is “technical data” subject to ITAR can be tricky. Many organizations find it challenging to continuously interpret and apply the rules.
- Continuous Compliance Management: Even after initial setup, maintaining end-to-end compliance for all AI data flows is hard. Employees may generate new prompts or use new models that weren’t anticipated. Ensuring every AI interaction stays inside the compliance “envelope” requires constant monitoring and updates.
- Third-Party AI Services: Many popular AI models are hosted by foreign or commercial providers that may not guarantee ITAR-safe handling. Verifying that an external AI API only processes data in U.S. regions (and that the provider staff are all U.S. persons) can be difficult. This often forces organizations to limit model choices.
- Performance and Cost Overheads: Encryption, filtering, and logging introduce overhead. Queries may run a bit slower, and hosting everything in U.S.-only environments (which can be more expensive) raises costs. Scaling the gateway to handle enterprise loads while preserving speed can be an engineering challenge.
- Shadow AI Usage: Without strict controls, users may try to circumvent the gateway by using unsupported tools or hard-coding API keys. Detecting and preventing such “shadow AI” usage is crucial, but not straightforward.
- Integration Complexity: The gateway must tie into many systems (IAM, logging, models). Ensuring compatibility and smooth operations across all these components can be complex. Organizations must also coordinate between security, IT, and development teams to manage the gateway effectively.
In practice, firms often underestimate these challenges. As one industry analysis notes, “ITAR compliance presents a series of challenges to organizations” – from misconceptions about what ITAR covers to the ongoing difficulty of controlling ITAR data. Overcoming these hurdles requires careful planning, organizational commitment, and sometimes cultural change. Despite the effort, though, the risk of failing to comply (with its heavy penalties) makes it imperative.
Conclusion
As AI becomes central to innovation in defense and aerospace, ensuring that these powerful tools obey export regulations is critical. An ITAR-compliant AI Gateway provides the necessary control layer: it acts as an “AI firewall” that enforces ITAR’s strict requirements while still enabling productive AI us. By combining robust security (encryption, authentication, logging) with AI-specific policy enforcement (content filtering, model routing), the gateway helps enterprises unlock the benefits of AI without risking regulatory breaches.
In summary, ITAR compliance for AI is achieved through careful design and governance. The gateway must operate inside U.S. jurisdiction, encrypt all data, authenticate every user, and keep an audit trail of all interactions. While implementing such a system involves technical and organizational challenges, it is ultimately what makes the use of AI defensible in regulated industries. With the guidelines outlined above, organizations can confidently adopt generative AI in defense contexts, trusting that their data and queries stay on the right side of ITAR.
Built for Speed: ~10ms Latency, Even Under Load
Blazingly fast way to build, track and deploy your models!
- Handles 350+ RPS on just 1 vCPU — no tuning needed
- Production-ready with full enterprise support
TrueFoundry AI Gateway delivers ~3–4 ms latency, handles 350+ RPS on 1 vCPU, scales horizontally with ease, and is production-ready, while LiteLLM suffers from high latency, struggles beyond moderate RPS, lacks built-in scaling, and is best for light or prototype workloads.







.webp)










